How To Flip Off All Notifications On Windows 10: A Simple Information
When your notifications are off, you’ll be more current for those that matter most. Several third-party apps claim to supply automated shutdown options for iPhones. However, because of iOS restrictions, these apps may not instantly shut down your gadget however can offer reminders or help in setting up routines that help you bear in mind to show off your iPhone. By minimizing the variety of notifications, you cut back the load on your telephone’s processor and reminiscence.

The advantages of turning off notifications – from better focus and productiveness to decrease stress and higher quality leisure time – can actually be life-changing. In a interval of data overload and fixed connectivity, uninterrupted stretches of time are a rare present. Claim more of them by disabling some notifications today, and revel in higher quality of life and well-being. Set up a distraction-free bedtime routine by silencing notifications (or enabling “do not disturb” mode) a minimal of an hour before mattress.
Managing notifications permits you to spend more uninterrupted time on tasks, growing overall productiveness. I have just lately also taken to turning off my social media notifications or deleting the apps altogether. These apps are designed to seize our attention and encourage us to spend as much time as potential utilizing them. The abundance of information I see daily on TikTok and Instagram could be overwhelming.
Those high in FoMO have a tendency to spend extra time on-line and examine their smartphones extra frequently. They also report extra frequent distractions from their digital units. In this examine, Liao and Sundar discovered that the tendency for silencing the telephone to extend phone-checking was particularly sturdy for these high in FoMO.
You can see this sort of habits in functions like antivirus and firewall. In these instances, you have to disable notifications for that app by altering its settings. The System part contains a wide range of choices, such as display, sound, notifications, and more. This is the place you’ll have the ability to handle many important options of your laptop.
Another reason to turn off preview messages is to protect your privacy. If you have delicate or confidential information in your notifications, you might not want others to see it. Turning off preview messages can help you preserve confidentiality and keep your private or skilled info private. I used to struggle with fixed notifications myself, however by turning most of them off, I managed to regain my focus. Most Windows PC owners use Outlook or Windows Mail as their mailing apps.
It is this thriller that additionally contributes to the strong urge to examine our telephones. Moreover, managing notifications can even help conserve your phone’s battery life. Every notification illuminates your display screen and consumes power, so limiting these alerts will contribute to a longer battery life. Additionally, by controlling the circulate of information, you can ensure that the notifications you do receive are relevant and important, offering you with solely what you deem essential. In abstract, turning off work notifications can lead to higher psychological well being, increased efficiency, and improved private relationships.
You can even remove and disable Copilot when you’re not thinking about utilizing AI. After you full these steps, your laptop will no longer bombard you with notifications. Instead of dealing with constant interruptions, you’ll have a more peaceful and productive time using your device. Look for extra choices to customise your notification settings further. You’ll see varied options for fine-tuning your notification preferences, corresponding to turning off sound alerts or even deciding which apps can hassle you.
Turning off notifications also can result in increased self-awareness and introspection. When people aren’t continuously distracted by notifications, they will give attention to their thoughts, emotions, and behaviors, leading to a deeper understanding of themselves and their motivations. This elevated self-awareness can result in private growth and improvement, as people can establish areas for enchancment and work on turning into better variations of themselves.
We communicate every day – with our household and friends, colleagues, and strangers. But how, when and where we communicate to totally different individuals varies depending on a selection of factors. With the powerful instruments Apple supplies you might have unprecedented management over when and how alerts attain you. Toggle off Allow Notifications to fully cease all alerts from that app.
Social media and expertise have allowed us to strengthen relationships with family and pals, close to and much, via constant communication. However, using screens, even people who help face-to-face conversations, shouldn’t be an alternative choice to growing in-person relationships offline. By unplugging, you may be fully current, immersed and engaged in conversations and activities along with your loved ones to create memories and experiences collectively to strengthen your bond. Another instance can be LinkedIn or Twitter, which each provide you with granular controls for receiving DM notifications however muting updates and follows.
This helps preserve a balance between staying knowledgeable and minimizing distractions. Many apps continue to run within the background to examine for updates and send notifications. Turning off notifications can cut back this background exercise, liberating up system sources that may in any other case be used to handle these tasks. Each notification consumes a portion of your cellphone’s battery, because it requires the device to get up, process the notification, and typically show it on the display screen.
Furthermore, turning off notifications can even assist people develop a more healthy relationship with technology, recognizing that devices are tools to be used, somewhat than masters to be served. Always tailor your notification settings primarily based on your workflow, privacy needs, and distraction threshold. Managing notifications successfully can lead to improved productiveness, decreased stress, and a more focused digital surroundings. We have all been there – waking up and looking out straight at your social media before you could have had the chance to really get up.
This round-up just isn’t in a selected order or targets a particular set of users. These are options that are usually a good suggestion to turn off to enhance the overall experience while minimizing distractions and clutter. In today’s fast-paced world, distractions appear to pop up in all places, pulling us away from what actually issues. I’ve discovered that my cellphone buzzes and dings on the most inconvenient occasions, making it powerful to give consideration to my duties or get pleasure from a peaceable moment.
The reply lies within the psychological factors that drive this determination. Some individuals might really feel overwhelmed by the fixed stream of notifications, resulting in feelings of hysteria and stress. Others might acknowledge the negative influence of notifications on their productiveness and focus, opting to remove distractions and enhance their work-life balance. In today’s digital age, notifications have turn out to be an integral part of our computing expertise. They maintain us knowledgeable about updates, messages, reminders, and various different alerts. However, extreme notifications can usually turn out to be distracting, overwhelming, and even intrusive, affecting productivity and focus.
Once you complete the steps, the feature should now be disabled on Windows eleven. The Widgets board can be useful to give you fast entry to data out of your favourite apps. However, by default, Microsoft additionally reveals its news feed from the MSN network, which normally does not add worth. In a latest update, Windows eleven received an update to show off this characteristic. In this how-to information, I’ll equip you with the expertise needed to navigate Windows eleven’s settings confidently and selectively turn off those options that do not align with your computing goals. Most are, but make certain you don’t disable critical system alerts that might impact your computer’s well being or security.
Turning off Instagram notifications is a good way to reduce your nervousness, focus on your objectives, and sleep higher; It can be one of the best ways to reduce distractions in your life and be extra productive. Once you’ve disabled app notifications in Windows 11, it’s a good suggestion to restart your pc to apply the changes. Simply click on on the Start button in the bottom left nook of your display screen, click on the power button, after which choose “Restart” from the drop-down menu. In equity, the platforms and corporations liable for this mess have tried intermittently to clean up. Instead, the Watch turned your wrist into yet another buzzable floor, this one even more durable to ignore. After years of torturing users, Apple lastly made it simpler to dismiss all your notifications at once.
Disabling notifications on Windows 11 could be achieved through varied methods, relying on whether you favor short-term silencing or permanent disabling. Below, 18 members of Forbes Technology Council talk about a couple of of the many advantages of often turning off our mobile units. If some nice benefits of switching off your e mail notifications sound good to you, you’re in all probability already questioning how you can do that.
You know the kind—hours gone in a blink, followed by that sinking feeling of remorse. A few months today, I determined to turn off all notifications for the social media apps I used most frequently. No pins, no banners, no pink badges reminding me of messages, likes, or someone going live. And make no mistake, notifications are extremely efficient at capturing our consideration. The purpose for this has to do with each the personalization and mystery of the notification.
Focus Modes sync throughout your iPhone, iPad, and Mac when Share Across Devices is enabled, ensuring a consistent distraction-free experience irrespective of which device you utilize. However, there are additionally different methods in which you’ll cope with them corresponding to using Instagram less typically or blocking sure accounts you follow so that you’re not disturbed after they make new posts. If you’re operating a business, you can also follow your rivals so that you’re notified of their activities, and might use that to your benefit.
We have all the instruments you need to confidently power down and block digital distractions. Start your journey to a happier, healthier you at present with a free trial of Freedom. Have you ever skilled that gritty, dry sensation in your eyes after an extended day in front of the telephone or computer? That’s just one of many many signs of eye pressure, a typical condition exacerbated by extreme display time.
Each ping and buzz attracts our attention again to our units, disrupting our focus and productiveness. By turning off pointless notifications, you’ll be able to reduce distractions and reclaim priceless time for more meaningful actions. Consider which apps really require quick alerts and disable the remainder.
I’ll guide you through deep cleaning your notifications—and share what life is like on the opposite side. Disabling notifications could feel uncomfortable at first if you’re used to being at all times reachable. Reuniting with your powers of attention and focus in a world of constant distractions is extremely rewarding. Detoxing from a gentle stream of provocative headlines, controversy and dire breaking news can even do wonders to assuage stress and nervousness. When you are feeling more targeted and constructive, you are in a better headspace to be current along with your priorities.
Notifications may be addictive, triggering a release of dopamine in our brains. This can create a vicious cycle of craving and looking for out constant updates. By turning off notifications, you’re breaking free from this cycle and regaining control over your behavior. The assumption is that being conscious of every message and alert creates an irresistible urge to search out out what’s behind that notification chime. So, turning off notifications ought to make it easier for folks to easily overlook about their smartphones.
(Sorry, Android users.) For example, should you’re attempting to limit how often you check your e-mail, you can use scheduled summaries to receive a digest of e mail alerts at specific occasions. Now that you have got a list of must-have alerts, set some time aside in your day— maybe put on music or a movie—and start culling your notifications out of your device settings. When you are prepared, attempt a half-day to a full weekend with all notifications disabled. Notice the method it feels to be in cost of whenever you check your messages and feeds. Reflect on what sorts of notifications are actually useful versus distracting. See should you really feel more grounded, productive or related during this digital downtime.
You can obtain a similar consequence to disabling the notification sounds by preserving your telephone in Do Not Disturb mode. You might select to do that only at sure instances of the day, such as when you’re working and sleeping, or you could simply depart the phone in that mode all of the time. It’s necessary to take control of your notifications and set boundaries to disconnect and take regular breaks from your phone. Whether you’re working on an important project, participating in a gathering, or just in search of a quieter digital surroundings, understanding the means to turn off notifications on Windows 11 is essential.
Remember, it’s not about abandoning social media altogether; it’s about being conscious of how we use it and taking management of our on-line experience. So, dare to silence the noise, and uncover a world where you’re in charge, not your notifications. A like right here, a DM there—it’s all engineered to keep us checking, scrolling, staying engaged, and glued to our phones. But someplace along the method in which, I realised I was continually reacting to my cellphone quite than interacting with it by myself terms. Recent phones typically have built-in tools that you have to use to observe your notification exercise and overall display screen time. By maintaining a tally of how you’ve used your cellphone, you probably can work out which notifications had been useful and which have been unproductive, then make informed decisions about what to cut down.
Using Instagram’s own settings permits for extra nuanced control over your notification preferences. Focus Modes help Focus Filters, which let you control what content material you see inside apps throughout a Focus. For instance, in the Calendar app, you can show only work events during Work Focus or disguise private chats in Messages.
In this text, we’ll explore complete strategies to turn off notifications on Windows 11, ensuring you probably can optimize your system based on your preferences. Turning off notifications also can result in improved time management and goal achievement. When people aren’t continually distracted by notifications, they can create schedules and plans that are extra sensible and achievable. By avoiding the constant stream of data, people can keep targeted on their long-term objectives, rather than getting bogged down in short-term distractions.
In Focus Assist settings, you’ll be able to set particular hours during which notifications are muted. Let your self settle into a brand new rhythm—one where your attention belongs to you, not your notifications. Waiting in line on the grocery retailer became a time to observe and breathe as a substitute of checking Instagram.
By taking control of your notifications, you can create a quieter, extra serene computing environment. This wasn’t a deliberate digital detox or some grand act of revolt agains know-how. I was having a sort of days where my telephone just wouldn’t stop buzzing—an Instagram alert when somebody I comply with went live, chat memes, someone tagged me to like a random Facebook web page.
They tracked photographs that alternated between mountain scenes and cities. Prior research has shown that efficiency tends to drop off as people age, but to the researchers’ surprise, after the web break, there was a significant increase in scores. “The effects on attention have been about as giant as if individuals had turn into 10 years youthful,” Castelo says. “What we discovered was that individuals had better mental health, higher subjective well-being and better sustained attention,” says Adrian Ward, a psychologist at the University of Texas at Austin. Researchers studied what happened when individuals agreed to block the internet from their smartphones for just two weeks. Keep up with your friends and family who’re posting daily updates; If you want to know what your mates are as a lot as, you presumably can observe their Instagram accounts.
The digital panorama is awash with notifications, and generally, switching them off is the only method to get stuff carried out. A lot of analysis has been accomplished on how a telephone affects the brain when it comes to radiation and most cancers involvement with not many convincing outcomes. However, one factor is for positive that the phone is altering our behaviour, psychological well being and well-being as nicely.
I stopped giving my telephone permission to interrupt me whenever it wanted. I started reclaiming the space in my day that had been slowly eaten away by alerts and reminders. While I tried to maintain my presence in social settings, I didn’t feel present in my own life. Blog writing sessions received derailed by “just checking real quick” moments that was 30-minute scroll fests. Even downtime didn’t really feel restful as a outcome of I was by no means absolutely disconnected. So, almost without pondering, I went into my settings and toggled off my notifications.
This can result in elevated feelings of connection, neighborhood, and belonging. Worse, that constant connection also can take a toll on your high quality of life and overload your senses. That’s why taking a break out of your quite a few social media apps and a while away from screens may assist be good in your psychological and physical well being. Designating screen-free zones in your house can be a powerful approach to break away from the constant pull of know-how. By creating designated areas the place screens are off-limits, you can domesticate a more aware approach to know-how use and foster deeper connections with loved ones. Creating a distraction-free setting can significantly impression focus ranges.
If you wish to focus your consideration in the workplace, turning off your notifications is the smart and apparent thing to do. If you are new to this function, take a glance at Apple’s assist docs to find out about all the available settings. Perhaps you turned off notifications from an overzealous app, but you want alerts in only particular situations. For example, exercising before work is my daily ritual, however I only want alerts for health apps after I’m really working out. For instance, I was stunned that Google Maps stored sending me alerts about reviews I left. When I reviewed the app settings, there was an inventory of notifications nonetheless on, despite the precise fact that I don’t remember setting these as a lot as begin with.
You can disable this function if you wish to declutter the Taskbar even additional or make room for other apps. If you don’t find the net highlights on the home page from Search, that’s one thing you presumably can turn off. These notifications can be found beginning with the drop characteristic update (Moment 3), but the choice to disable the function is still in preview. After you full the steps, the Start menu will now not show notifications for associated details about your Microsoft account.
Morning coffee grew to become a peaceable ritual quite than a content catch-up. I started noticing things again—the method gentle filters via my front room, the birds flying past my window. I felt more current in my own life, somewhat than distracted by everybody else’s. This small shift has made me feel extra in control of my time and vitality. I used to really feel a delicate strain to reply instantly or “keep up” with every little thing.
This prevents others from seeing when you’re on-line, assuaging the strain of responding to notifications instantaneously. Set schedules or automations to activate the Focus based on time, location, or app usage. You also can allow Smart Activation, where your iPhone learns when to activate Focus routinely based mostly on your habits. Customize your Home Screen and Lock Screen to show particular pages or dim the display screen to minimize distractions.
But when telephones are silenced, individuals do not know if they have messages or not. So they will verify their phones much more incessantly than they really obtain notifications, so as to be sure that they are not lacking anything. And that is especially true for people who are already overanxious about lacking out on what others are doing. Whether you’re engaged on an necessary project or simply need some peace and quiet, understanding the means to handle notifications is important. You can all the time revisit these settings when you change your mind later on.
Once you’re within the Settings window, you’ve opened the gateway to manage just about every little thing on your pc. This text was generated utilizing a big language model, and select text has been reviewed and moderated for functions such as readability. Sure, removing the cellphone is a straightforward method to pressure that conversation to occur. And it was so much simpler to break freed from my phone than I thought it would be. You know the benefits of not using a phone – but how do you stop utilizing it? You’ll discover much less stress, more well-being, and the power to connect more authentically with your thoughts and emotions.
Setting your telephone apart will allow you to focus on issues you should get carried out. To allow notifications once more for an app, toggle the switch to “On” and you’re accomplished. If that’s the case, right here is how to disable Windows 10 notifications completely. Being a disciplined individual in virtually all elements of my life I thought I may win with the power of will.
Unplugging minimizes distractions and increases your capability to focus on the task at hand. Yes, you can flip off notifications for a particular period of time on Messenger. This function is helpful if you would like to take a break from notifications for a couple of hours or days.
Under the “Notifications” section, toggle off the notifications you want to disable. In the Settings menu, choose “System” to access system preferences. Since our prehistoric ancestors used stone tools to begin fires and hunt for prey, expertise has made us more environment friendly and efficient at what we do. It has introduced us convenience, improved communication, and — relatively talking — long and comfy lives. Pureinfotech is independent on-line publication that makes Windows and apps simple to grasp with clear, concise guides, recommendation, and news.
This can lead to improved relationships, increased job satisfaction, and a better general high quality of life. Awareness is vital to creating positive modifications, and tracking your display screen time provides priceless insights into your habits. Most smartphones now provide built-in instruments to monitor app usage and display screen time statistics. Take advantage of these features to determine which apps are consuming essentially the most time and vitality. Are you mindlessly scrolling by way of information feeds throughout your downtime? By pinpointing your largest time sinks, you probably can take proactive steps to restrict their affect and regain control of your digital life.
Adjust sound notifications can do an enormous distinction in user expertise. Every time we obtain a model new notification on our phone, the sound and vibration can interrupt our concentration and even bother these around us. That’s why customizing sound notifications is a very useful feature that enables us to adapt our gadget to our particular person needs and preferences. If you wish to fully flip off the notification sound, listed here are some choices and steps to observe to realize this.
Unplugging encourages you to move your body and get regular train, which is essential for heart well being, bone energy, sustaining a wholesome weight, improved temper, better sleep and so much extra. Turning off electronics allows you to step away from the constant barrage of online data to provide your mind an opportunity to rest and reset. Once your mind is “recharged,” your focus, decision making and artistic pondering can enhance. It’s incredible how rather more vivid life is when you take a couple of hours with out that crux. I slept higher, centered more, grew as an individual, and enjoyed the unbelievable country and folks. Chances are they had been asleep or had put their phone away like normal people do and have been simply residing life.
Urgent communications will still get by way of to you, as you can permit notifications from particular important senders or keywords even while silencing the remainder. The thought is solely to attenuate frivolous distractions so you should use technology as an empowering device by yourself terms. Giving something your full, undivided attention magnifies its benefits and immerses you within the expertise extra fully. By turning off notifications, you set firmer boundaries around your consideration and availability. You communicate to the world (and yourself) that you just aren’t at the mercy of every interruption or request. This can present a great sense of aid and management over your time and headspace.
Constant notifications can create a way of hypervigilance, leading to elevated stress and nervousness ranges. By turning off notifications, individuals can reduce their stress levels and create a way of rest and calm, resulting in improved mental well being outcomes. Additionally, turning off notifications may help people avoid the fixed comparability and competition that may come with social media, resulting in increased self-esteem and body satisfaction. The psychological benefits of turning off notifications embrace lowered stress and anxiousness, improved mental clarity, and elevated sense of control. When notifications are continuously popping up, it could possibly create a way of chaos and dysfunction, leading to emotions of overwhelm and nervousness. By turning off notifications, people can create a way of calm and tranquility, permitting them to think more clearly and make higher selections.
Understanding how notifications work on Instagram is essential to managing them effectively. Instagram supplies users with numerous forms of notifications, together with likes, feedback, follows, messages, and numerous updates from accounts you comply with. While these alerts can improve engagement with the platform, they can also lead to emotions of stress or anxiety if they turn into extreme.
I’ve found that by reducing those fixed interruptions I can dive deeper into my duties and truly get pleasure from what I’m doing. If you’re seeking to reclaim your peace and quiet whereas working in your pc, following these steps will assist disable notifications on your Windows 10 system. You’ll have the power to stop these distracting pings and concentrate on what’s necessary. Also, remember to schedule “do not disturb” hours or “tech-free times” to guarantee that you’re not interrupted by notification “dings” or unnecessary digital updates. Unplugging enables you to disconnect from the constant stream of information and as an alternative reconnect with yourself, loved ones and the world round you in a significant way. Putting down your display allows you to recharge your thoughts and physique to improve your psychological health, general well-being and quality of life.
These move states often characterize the greatest supply of success in our lives. Notifications additionally reduce productiveness by inflicting us to shift from one cognitive task to a different. When you might have notifications continually bombarding you, it could feel like you have to respond to every little thing proper now. If somebody wants to reach me, they know they can call, textual content, or e mail. Not every thing requires an prompt response, and because it turns out, not a lot is really essential and pressing.
Previously she was a public radio journalist, so she has a lot of opinions about microphones. When she’s not writing or tinkering with Zapier, Krystina enjoys sewing her personal clothes and taking long naps in between her many hobbies. Like any deep-cleaning try, clearing out litter is much less complicated than sustaining order. Don’t assume twice, and click on No when an app or website asks to ship notifications. If you’re already residing that notification-less life, these ideas will also allow you to make your existing notifications more practical. As you get more intentional about when and the way you employ know-how, you may probably find yourself extra present, productive, and peaceful.
Windows 11, Microsoft’s latest operating system, presents a variety of options to handle notifications successfully, allowing customers to customise their experience and reduce undesirable interruptions. In our fashionable world, we’re constantly bombarded with notifications from our phones, computer systems, and different gadgets. Whether it is a new email, a text message, or a social media update, these fixed interruptions may be extraordinarily distracting. One means to assist scale back the impact of notifications is to use greyscale mode in your devices.
You may inform Outlook to notify you only when you get something out of your boss or partner. You might say “never send me coupons,” and ask each app to comply. You might have some notifications come via during work and shut off whenever you get home. Facebook might determine who you truly care about, and notify you accordingly.
They have extra to do with the objectives of the corporate which sends them. The Shortcuts app enables you to create custom shortcuts for various duties, together with mechanically turning off your iPhone at a specified time. There are several strategies to automatically flip off your iPhone at evening, starting from built-in options to third-party apps. Here, we will talk about the most effective and user-friendly methods. This information helps you’re taking control of your notifications, allowing you to give consideration to what really matters at work. Get the newest news, exclusive updates, and special content about know-how, gaming, anime, innovation, and much more directly to your inbox.
That being said, when part of your character is being obsessive about social media, you’ll find a way to lose observe of what really issues. By having these notifications turned off, you’ll only examine social media if you actually need to quite than whenever you really feel compelled to. This will let you mirror on different passions and pursuits, such as studying or writing. When you re-evaluate your priorities, you will really feel extra snug in taking a look at social media because it now not defines you or your day. I never thought one thing so easy as a documentary on the unfavorable aspects of social media could be the sole thing to alter the best way I use my social media apps, and but here we’re. For starters, I would like to say I was the type of one that started my day by taking a glance at these apps.
Many individuals battle with managing their notifications, and some of the irritating elements is coping with preview messages within the notification bar. In the rapidly evolving panorama of digital communication, notifications serve a crucial function however can also turn out to be sources of distraction. Mastering notification management on Windows eleven empowers you to create a balanced, distraction-free workspace. If you have an interest in turning off notification sounds, you can observe some helpful ideas. First of all, verify your gadget’s settings to find the option to show off notification sounds. This is normally positioned within the settings or configuration section of the gadget.
But turning the notifications off can actually have long-term mental health advantages. We obtained in touch with Dr Sonal Anand, Psychiatrist, Wockhardt Hospital, Mumbai to elucidate to us how. You can get off the notification practice, though, no matter when you’re drowning in alerts, you need to reduce distractions, or your optometrist has caught on to your screen behavior.
If you utilize social media for non-work functions whereas at work or share a computing device in your remote office, the next advice is essential. “Deep work,” popularized by famend skilled Cal Newport, revolves around achieving a state of undisturbed, concentrated focus on mentally difficult duties. This uninterrupted focus not only enhances the quality of our work but also permits us to deal with intricate problems and unleash our creative capacities. Approaching work in a more aware method permits us to be more present, which in flip fosters a deeper sense of satisfaction and fulfillment. With the absence of constant interruptions, we will deal with the ocean of information overload more successfully, fastidiously selecting the info that truly deserves our consideration. You can reduce notification frequency by turning on scheduled summaries in your iPhone.
Without the constant interruptions, I might actually get right into a state of flow—whether I was designing at work, writing a weblog submit, or simply watching a movie. These notifications wouldn’t be of a lot concern however for the very fact they are disruptive. They stop us from entering flow states, that are durations of intense focus in which we lose ourselves to the moment.
The blue light emitted by smartphones can suppress the production of melatonin, the hormone responsible for regulating sleep. By turning off your iPhone, you can minimize your publicity to this blue light and create a sleep-conducive environment. Additionally, the fixed notifications and alerts out of your cellphone may be distracting and make it difficult to go to sleep. By turning off your iPhone, you’ll find a way to keep away from these distractions and enhance the quality of your sleep. Both Android and iOS allow you to go into your settings and select individual apps to customize your notification preferences.
If you see inaccuracies in our content material, please report the mistake via this kind. When you click on by way of from our website to a retailer and buy a services or products, we may earn affiliate commissions. This helps help our work, however doesn’t have an result on what we cowl or how, and it doesn’t have an effect on the value you pay. Neither ZDNET nor the creator are compensated for these independent critiques.
You can usually choose to turn off all notifications for a specific app, or select specific types of notifications you need to receive. In today’s fast-paced and hyper-connected world, distractions appear to be everywhere, hindering our capacity to remain targeted and be productive. With notifications from apps and devices continually vying for our attention, it’s no wonder that many of us wrestle with a declining consideration span. I continually see headlines touting various ways to be more productive, and a simple Google seek for the phrase “Productivity Hacks” returns at least 30,900,000 outcomes. It’s safe to say that everyone is in search of ways to restrict distractions and get extra done. Checking notifications in batches at set instances, somewhat than letting them interrupt you constantly, places you back in the driver’s seat.
In the case of iOS, from Settings, decide Screen Time then Downtime. You’re able to set certain hours at night when solely certain apps will work, notifications and all. It’s an excellent possibility when you need something more granular than Do Not Disturb. You may find it extra helpful to mute all of the notifications on your telephone overnight, but if it’s only one or two apps inflicting you issues, app-by-app settings might be the means in which to go.
It’s all the buzzing and dinging, endlessly calling in your consideration. A Deloitte study in 2016 discovered that people have a look at their phones 47 times a day on common; for younger people, more like eighty two. Apple proudly introduced in 2013 that 7.four trillion push notifications had been pushed via its servers. So, are you able to take charge of your display screen time and reap the rewards in your mind and body? Well, say hiya to Freedom—your new sidekick within the battle towards display overload!
Intermittent Fasting: Tips On How To, Sorts, Advantages, And Security
In addition to promoting weight management and balanced blood sugar control, intermittent fasting may assist scale back irritation and shield in opposition to continual diseases similar to diabetes. Intermittent fasting refers to an eating cycle that features periods of fasting of round 12–36 hours. Many proponents of intermittent fasting report improved weight management. 16 hours is kind of the magic number for fasting — as in, it’s the commonest time frame folks intermittently quick to keep up a healthy physique weight, among different advantages. Fasting is an efficient way to safeguard your metabolism, however it’s also a good way to assist the well being of the rest of your physique, together with your immune system. Studies have proven (14) that intermittent fasting can upregulate proteins that protect us from obesity, diabetes, and metabolic issues, Alzheimer’s disease, and neuropsychiatric problems.
This supplement will assist you to go to sleep and keep asleep so that you wake up refreshed and recharged. Defend is designed to promote a wholesome, vibrant immune system whereas simultaneously concentrating on immune-related growing older hallmarks. These statements haven’t been evaluated by the Food and Drug Administration.
It’s a easy dietary behavior that’s not tough to use, and the most effective thing about it’s that you just won’t have all the everyday dietary restrictions that include other regimens. This has a quantity of health advantages, however is especially helpful when it comes to weight loss and physique composition, because it prompts your physique to use stored fats for gas. After a selection of hours without food (the exact time interval varies depending on numerous totally different factors), your body may have burned up most or all of its saved glycogen. If, like most individuals, you eat three to 5 meals per day (with some snacks thrown into the mix), your physique by no means breaks out of this cycle. So limiting your calorie consumption — even substantially — does not essentially affect this process.
Studies indicate that intermittent fasting reduces fasting blood sugar ranges by 3-6% and insulin resistance by 20-30%. Lower insulin ranges mean decreased arterial inflammation and plaque buildup, which lowers the danger of atherosclerosis (hardening of the arteries). A examine printed in the World Journal of Diabetes found that intermittent fasting in adults with kind 2 diabetes improved key markers for those people, together with their physique weight and glucose levels. Another research found that intermittent fasting was as efficient as caloric restrictions in decreasing visceral fat mass, fasting insulin and insulin resistance.
You may try totally different intermittent fasting (IF) plans to determine what works finest for your metabolism and overall health. Some people mix IF with a ketogenic or low-carb food plan for added weight reduction benefits. These blood sugar benefits had been doubtless driven by weight reduction, Varady says. But Peterson thinks people of all body sizes might enhance their blood sugar with time-restricted consuming, even with out shedding weight. For the best outcomes, it is essential to eat a healthful and balanced diet on nonfasting days.
In an animal study, IF improved glucose homeostasis by preserving pancreatic β-cell mass through the autophagy-lysosomal pathway in diet-induced obese diabetic mice 73. Human research are needed to completely perceive how intermittent fasting may affect reproductive health. It may assist to set timers at each the start and the end of your consuming window to remind you when to begin out and cease eating. Intermittent fasting is an consuming plan the place you alternate between eating and never consuming for a certain amount of time. Children and adolescents are nonetheless rising and need consistent vitality consumption. They shouldn’t engage in extended fasting unless supervised by a medical skilled.
Moreover, IF might help protect lean muscle mass, which is usually lost during calorie restriction. By promoting fats loss while sustaining muscle, intermittent fasting could help a more healthy metabolic price over time. One of probably the most well-documented benefits of intermittent fasting is weight reduction. Studies show that individuals following IF diets can lose an identical or greater quantity of weight in comparability with those following conventional calorie-restricted diets. A 2020 meta-analysis in JAMA Network Open found that intermittent fasting can lead to reductions in physique weight, body fat proportion, and waist circumference.
Fasting therapy improved stomach ache, diarrhea, nausea, and anxiousness in a medical trial on fifty eight individuals with IBS 31. It’s finest to talk with a health care provider earlier than making drastic changes to your consuming habits, especially in case you have an underlying health situation. If somebody is fasting for well being causes, it’s essential that they do it safely and for no longer than is necessary. People should at all times converse with a healthcare skilled first if contemplating fasting.
Inflammation, which is linked to numerous persistent ailments, additionally seems to lower with intermittent fasting. During fasting intervals, your body produces fewer inflammatory markers, similar to C-reactive protein and pro-inflammatory cytokines. This discount in inflammation can profit not solely coronary heart health but in addition joint ache and other inflammatory conditions. During the primary few days of intermittent fasting it’s common to experience a decrease in vitality levels and increased starvation. This is as a outcome of your body remains to be adapting its metabolic processes to finally ramp up burning body fats and ketones for energy. Other results have come from Satchin Panda’s lab on the Salk Institute for Biological Studies in La Jolla, California.
Only water, black coffee or tea is allowed to maintain your body within the fasted state. If you are considering intermittent fasting, ensure to discuss it with your doctor. Skipping meals and severely limiting calories may be dangerous for individuals with sure conditions, such as diabetes.
You might assume the goal of your journey is weight loss when it’s really fats loss. This occurs as a outcome of if you shed pounds, you lose a combination of fat, fluid, muscular tissues, and organ measurement. Animal studies counsel that intermittent fasting may help prevent cancer, though these outcomes are yet to be verified in people. The proof to support health enhancements in folks is promising, but many of the clinical research thus far have been relatively short-term interventions over a interval of months. However, in somebody with diabetes, the pancreas doesn’t make sufficient insulin, or the body does not use insulin successfully.
At final, we examined whether or not IF is more practical for mind and cognitive functioning depending on the type, quantity and timing of dietary intake. There is variability in the way IF is practiced, yet related differences between (effects of) these variants are currently not sufficiently accounted for within the literature. As IF and CR set off the identical mechanisms 175, a caloric reduction throughout IF would possibly further strengthen neurological health benefits. Specifically for overweight topics CR during IF would possibly result in more optimistic results since all forms of IF (with the exception of TRF) lead to weight loss 211. There have been constructive results for FMD, which includes fasting combined with a low protein/amino acid diet.
Intermittent fasting, also called cyclic fasting, has risen in reputation in current times as more analysis emerges showing that it’s typically protected and effective. Electrolyte imbalances and dehydration are among the many most typical causes for keto-flu symptoms and are linked to weakness, lightheadedness, muscle cramps, and complications. Water fasting isn’t really helpful as a outcome of it can enhance your threat of electrolyte imbalance.
Because our our bodies conserve power throughout fasting, our basal metabolic rate (the amount of vitality our bodies burn while resting) turns into more efficient, thereby reducing our heart price and blood stress. For many individuals, somewhere between 14 and 18 hours of fasting per day is the perfect vary, offering extra vital weight reduction benefits than a 12-hour quick, while nonetheless being attainable, says practical practitioner B.J. The diversity in intestine microbiota composition is decided by a quantity of factors, of which diet is a major one in addition to dietary timing 57. The abundance of ±15% of microbiota dynamically oscillates in exercise and relative abundance throughout the day in response to circadian and hormonal fluctuations and moments of dietary consumption 58,59.
Weight loss, improved metabolism, and better psychological readability are just a few of the advantages. Plus, many discover that it helps them develop a healthier relationship with meals. “A balanced meal should have fiber-rich carbs, protein, some wholesome fat, and colourful fruit and veggies,” Palladino says. To monitor your nutrient intake, she recommends breaking your plate into quarters. Fill 1 / 4 with protein, another quarter with a starchy vegetable (like candy potatoes) or carb (like quinoa), after which the remaining half with fruits and vegetables.
Intermittent fasting includes biking between durations of consuming and fasting. While it could have a variety of the identical well being benefits as a food regimen, it’s really an consuming sample. It means you fast (don’t eat) during a certain time frame each day (usually an prolonged period of time). You then eat during another time frame each day (usually a smaller period of time). While you’re fasting, you can drink beverages that don’t include energy, including water, black coffee, and unsweetened tea. Fasting for eight or 10 hour periods was found to improve blood sugar and ldl cholesterol and to lower ranges of hemoglobin A1c, according to a 2024 short-duration research in 108 individuals in Annals of Internal Medicine.
Some well being professionals consider intermittent fasting may steer people away from wholesome consuming suggestions, similar to consuming five parts of fruit and veggies a day. Many worry fasting can also set off eating disorders or binge eating. According to Dr. Michael Mosley – writer of The Fast Diet books – this consuming plan can not solely help folks lose weight, however it presents an array of other well being benefits. The early time-restricted feeding plan works by limiting the number of hours you possibly can eat inside a day. Eight-hour and 12-hour plans can decrease insulin and blood stress and help maintain weight.
Minimal analysis exists on the results of intermittent fasting in certain populations, similar to pregnant or lactating women. A feedback system lets the body know when no extra glucagon is required. When every little thing works accurately, the physique will produce insulin to move glucose out of the blood and into the cells to rebalance the elevated glucose ranges. Exercise is actually very annoying on the body and when you’re doing it it’s not good, but as your physique adapts and make changes to cope with the stress of exercise you get health benefits.
Healthy Keto® is a low-carb, high-fat food plan focusing on nutrient-dense, high quality meals like wild-caught fish, wholesome fats, grass-fed beef, pasture-raised eggs, and organic produce. Alternate-day fasting is a type of intermittent fasting characterised by fasting each other day. A diet excessive in carbohydrates, processed meals, and sugar can lead to insulin resistance. Being obese or overweight is considered one of the major danger components for developing kind 2 diabetes.
My wife and I actually have been fasting using the 16/8 method since late 2018 and it’s now a part of our normal routine. As a result, we don’t even should make an effort anymore and we usually don’t really feel hungry through the fasting window. As we go through the totally different fasting methods, you’ll notice that it’s not as difficult as it sounds — and that you might have practiced intermittent fasting a few times already without even realizing it.
All the articles on HexaHealth are supported by verified medically-recognized sources corresponding to; peer-reviewed educational research papers, analysis establishments, and medical journals. Our medical reviewers additionally check references of the articles to prioritize accuracy and relevance. As one of the first useful drugs telehealth clinics on the planet, we provide webcam well being consultations for individuals around the globe. Eating wealthy and heavy meals too soon can overwhelm your digestive system and trigger nausea, bloating, diarrhea, and belly ache. Women may lose up to 7 pounds, and males 7-13 kilos within the first month. Glucagon does this by inflicting the liver to interrupt down glycogen (stored glucose) and release the glucose again into the bloodstream.
As a end result, people advanced to have the ability to perform with out meals for extended periods of time. Before you read about the benefits, note that a 72-hour quick is a critical endeavor. If you’re going to strive it, ensure you drink loads of water, get loads of electrolytes like sodium, magnesium, and potassium, and cease fasting when you feel lightheaded or otherwise unwell. This apply might help decrease danger components for age-related persistent diseases and assist immune system operate, intestine bacterial environment, and anti-aging processes.
It’s been used for hundreds of years during instances when food was scarce, and it even plays a central role in plenty of major religions. The primary rules of intermittent fasting are slowly transitioning into your chosen fasting schedule and constantly following your fasting routine. But scientists don’t know a lot about what occurs to your body when you quick. That work has offered early clues as to how periods without meals might have an result on the body. However, this fasting fashion can increase the danger of nutrient deficiencies if OMAD isn’t combined with a nutritious high-fat food regimen corresponding to Healthy Keto. OMAD can lead to disordered consuming in those with a historical past of binge consuming or anorexia.
“The longer-term studies confirmed that the positive results of intermittent fasting are not considerably different from those you’d have if you simply ate fewer energy daily,” Herzig provides. The best hours for intermittent fasting depend in your preferences and daily routine. Most folks discover it convenient to quick in a single day and thru the morning, have their first meal round lunchtime, and resume their fast after dinner.
Religious fasting also spans centuries, from Ramadan in Islam to Lent in Christianity and fasting rituals in Buddhism and Hinduism. In these contexts, fasting wasn’t nearly food; it was about self-discipline, purification, and connecting to the next function. Even Hippocrates, the father of recent medicine, advocated for fasting as a way of healing. Autophagy and insulin regulation assist cut back the danger of several cancers. Boosts BDNF (Brain-Derived Neurotrophic Factor) and may cut back the risk of neurological illnesses. It will increase ranges of norepinephrine, HGH, and other hormones that assist fat loss and muscle preservation.
The majority of our participants tried the IF food plan ranging from a month as a lot as three months, suggesting that this sort of food regimen is a short-term resolution for individuals attempting to lose weight. Side results have been reported in our results, with a variation of intensities (mild, reasonable, severe), significantly inside the first month. All in all, the majority of our respondents had been pleased with their experience and saw excellent weight loss outcomes with the IF food plan. Moreover, our statistics present that 67.3% of the individuals who adopted the IF food regimen also performed physical train, whereas solely 32.7% practiced IF without any physical exercise. Alexandra Ferreira Vieira discovered that those who did moderate aerobic workouts through the fasting state confirmed a big increase in fats oxidation 14. The IF food regimen is an environment friendly dietary plan for those aiming at a weight reduction journey over a brief length, ranging from less than a month as much as three months.
Fasting could increase the risk of deficiencies linked to untimely delivery, lowered IQ, and congenital disabilities. Though fasting is generally considered secure, breastfeeding or pregnant mothers ought to avoid intermittent fasting. Here are some concerns to ensure intermittent fasting is right for you. Watch the video under to be taught more concerning the basics of intermittent fasting.
Results for the sensitivity evaluation restricted to healthy individuals with floor underneath the cumulative ranking (SUCRA). There have been six distinctive meta-analysis comparisons for diastolic blood strain (DBP) 21, 25, 50, fifty four, 55 (Table 2). Only ADF considerably reduced DBP compared to traditional diets (− 3.forty one mmHg; − 5.ninety one to − 0.92) 25, albeit with very low certainty. In circumstances the place disagreements could not be resolved by way of consensus, a third researcher, L.-W.C., acted as an arbitrator in the course of the negotiation process. For each eligible article, we extracted effect estimates for consequence measures related to metabolic well being, together with anthropometry measurements, blood strain, glycemic parameters, and lipid profile.
Fasting will not be appropriate for everyone and will cause unwanted aspect effects. For example, when you have diabetes, fasting can lead to low blood sugar levels, which could possibly be dangerous. A evaluation published within the American Cancer Society Journal notes that intermittent fasting may profit the therapy and prevention of most cancers in some conditions. It may lower tumor growth and toxicity from chemotherapy in some folks. Another review showed that alternate-day fasting might considerably decrease blood stress, as well as levels of blood triglycerides, total cholesterol, and LDL (bad) ldl cholesterol. Some animal research suggests that intermittent fasting might lead to hormonal adjustments and undereating.
I began doing that as a outcome of prolonged fasts have unique well being benefits related to cell renewal and immune system help that you won’t get — a minimum of to not the same extent — with shorter fasts. While I’ve found it comparatively straightforward to maintain up a 16/8 fasting schedule, extending these fasts to 24 hours and past may be difficult. Some intermittent fasting strategies are fairly flexible and easier to observe than others. Intermittent fasting is easy to implement, but it’s an incredibly highly effective methodology for reducing weight and improving your general well-being. Balance fasting with nutrient-dense meals and hydration to take care of long-term well being. To fully perceive intermittent fasting’s potential, extra robust, long-term research is important.
Notably, a study carried out at the Johns Hopkins School of Medicine found that fasting for no less than two days per week can defend towards the buildup of amyloid plaques (amyloid-β). These plaques are a kind of protein that attach to neurons, and are increasingly believed to play a distinguished function in the improvement of Alzheimer’s. Intermittent fasting reduces fasting insulin ranges, which is amongst the markers of insulin resistance. Intermittent fasting improves your circulating levels of insulin and increases your body’s sensitivity to this hormone.
A RD works with you to ensure your food regimen is nutritionally full. A Season Health registered dietitian may help you navigate any unwanted effects like constipation that may occur with dietary modifications. Intermittent fasting has been proven to help decrease blood sugar ranges in those with extreme ranges as well as promote intentional weight reduction. More research is required, nevertheless, to find out if intermittent fasting fosters blood sugar management other than its effects on supporting weight loss, since weight loss is known to decrease blood sugar levels. A small 2012 examine tested Muslims with a historical past of coronary heart illness who fasted intermittently for Ramadan.
It may help scale back meals intake intermittently, which can supply well being benefits and help with weight management. In this text, we will discover intermittent fasting’s sorts, how it works, and its potential health benefits. Intermittent and periodic fasting (IF and PF, respectively) are rising as protected methods to affect longevity and healthspan by performing on cellular aging and illness danger factors, while inflicting no or minor unwanted side effects. We also talk about each the therapeutic potential and unwanted effects of IF and PF with a concentrate on cancer, autoimmunity, neurodegeneration and metabolic and heart problems. Periods of voluntary abstinence from foods and drinks (i.e., intermittent fasting) has been practiced since earliest antiquity by peoples around the globe.
When I’m fasting whereas traveling, I sip on hot tea all day.For a great video that explains the relationship between hunger and ghrelin, take a look at this hyperlink. And for extra particulars on this topic, learn my complete guide how to curb your starvation during a quick. The cause why intermittent fasting works for weight loss is pretty easy. After a meal, your body gets additional carbs, which will increase your blood sugar levels. During fasting periods, your physique makes use of those carbs in the vitality creation and metabolic processes.
Just just like the modified 2-day plan you will be eating clean for five days of the week. However, the other two days you won’t eat something for 24 hours and today have to be nonconsecutive. Everything you do eat will once more encompass wholesome fats, clear protein, and produce. Remember, you shouldn’t bounce proper into this plan when you haven’t intermittent fasted before.
Karen Davies, Senior Clinical Advisor at Diabetes UK, stresses it’s essential for anyone with diabetes to seek medical recommendation earlier than altering their food regimen. “For folks with Type-2 diabetes who’re taking certain drugs or insulin, intermittent fasting can increase the danger of low blood-sugar levels”, she provides. Fasting has been shown to guard neurons and ameliorate cognitive impairment in animal models119. The latter study did not detect reduced ranges of Aβ after restriction of essential amino acids, although it did observe decreased accumulation of phosphorylated Tau in the hippocampus121. This means that fasting and protein restriction can defend the nervous system even in the presence of excessive levels of Aβ, although their effect on the fibrillar versus soluble forms of Aβ stay poorly understood.
According to a 2022 article, fasting is a common weight loss technique. Fasting is a longstanding part of many non secular traditions, together with the Jewish and Muslim observances of Yom Kippur and Ramadan. A form of fasting often recognized as intermittent fasting has additionally gained reputation as a weight-loss tool. When selecting a fasting regime, it could be very important choose a way which fits in along with your lifestyle and schedule. By having a clear aim and choosing a regime that matches in with your life you’ll be more more doubtless to stick to it.
Intermittent fasting while pregnant could lead to insufficient intake of calories and vitamins, which might hinder fetal growth and enhance the risk of congenital disabilities. Intermittent fasting can produce visible results for weight reduction in a few weeks. Dieters who stick with regimented fasting and consuming periods can lose up to three kilos weekly. Obesity is a danger issue for many totally different cancers, so the burden loss side of intermittent fasting could possibly be liable for the reduced cancer risk that some studies hint at. Intermittent fasting may have benefits for diabetes prevention, as it can assist weight reduction and doubtlessly influence different elements linked to an increased risk of diabetes. Intermittent fasting could result in higher brain well being, possibly as a end result of decreased inflammation and oxidative stress.
In the diabetic state, IF reduces the plasma concentrations of glucose and insulin and elevates adiponectin levels 2,69. An further mechanism of IF is the metabolic swap between fed and fasting states. Fasting, particularly repetitive fasting, induces organisms to shift their metabolic part, which improves metabolic circumstances and extends well being expectancy 18. Furthermore, fasting activates autophagy and defense mechanisms in opposition to oxidative and metabolic stress and suppresses inflammation 28-31. These effects of IF are just like these of cardio exercise 32,33.
Scientists have studied the mechanisms behind those advantages and how they translate to people. He suggests aiming for a 16/8 schedule, but take a gradual strategy. For occasion, first strive a 12/12 schedule, where you eat during a 12-hour window and fast for 12 hours.

“But when you get off schedule for a day or two, you haven’t negated your efforts. Just decide it up again and keep going. Eventually, you would possibly even see intermittent fasting turn into part of your everyday life.” Still, the prevailing evidence of intermediate fasting’s benefits is restricted, and any long-term advantages or drawbacks are unknown. “Most research have not checked out giant populations and solely explored its impact over several weeks or up to one 12 months,” says Dr. Hu.
In addition, S6K1-mutant mice show a delayed onset of age-related phenotypes, similar to bone-matrix loss, immune and motor dysfunction and insulin resistance84. A tumor suppressor protein with an important position in cell-cycle arrest. And as a outcome of it really works superbly alongside pure cleansing, I typically guide purchasers by way of gentle liver-supportive cleanses while fasting.
The execs and cons of intermittent fasting are diversified, but the execs definitely take heart stage. These are a few of my favorite ways intermittent fasting targets totally different areas of your well being to restore your physique from the inside out. During a 48-hour quick, it’s important to drink plenty of zero-calorie fluids and replenish electrolytes.
It can be necessary for individuals with well being circumstances corresponding to diabetes to consult a healthcare professional before fasting. This sort of intermittent quick could additionally be helpful for somebody who has already tried the 12-hour quick but did not experience any advantages. The best way to follow the 12-hour fast is to include the interval of sleep in the fasting window. There are numerous strategies of intermittent fasting, and other people will prefer completely different types. Read on to search out out about six different ways to do intermittent fasting.
Intermittent fasting additionally adjustments your hormones to make use of fat as gas, which helps you shed pounds. Intermittent fasting results are often much like these achieved via the ketogenic food plan, and the two may be combined. However, intermittent fasting methods present the chance to shift your body’s metabolism with out having to change the meals you eat or undertake any specific dietary guidelines. However, I would not suggest beginning an intermittent fasting program and the keto food regimen at the similar time.
It’s additionally crucial to focus on eating nutrient-dense, whole meals throughout your eating window. This supports total health, prevents nutrient deficiencies, and helps you shed pounds. Furthermore, by stabilizing insulin ranges, intermittent fasting may help relieve post-meal fatigue, leaving you with better focus and extra vitality all through the day. Around the 16-hour mark of a fast, the physique triggers autophagy, a process that recycles old, damaged cells and helps get rid of pathogens. This can cut back the danger of a number of illnesses, including infections, neurodegenerative disorders, and most cancers, while selling longevity.
This might be because intermittent fasting syncs your food consumption together with your circadian rhythm, or physique clock. Eating in accordance with your body clock is helpful for processing glucose and decreasing your danger of diabetes. Since food is a major element of many social gatherings, intermittent fasting could cause issues with meals and social actions. It could be difficult to observe a fasting schedule when going to social gatherings or consuming out. Once your physique runs out of sugar, your insulin levels drop, and your body begins breaking down fats cells to use as gasoline. This process, lipolysis lipolysis The breakdown of saved fats (triglycerides) into fatty acids and glycerol for power use.
All members had been additionally instructed to take care of their usual day by day bodily activity throughout the trial, to remove this variable and to isolate the timing of meals intake as the one distinction between the two teams. Short-term calorie restriction plans, similar to intermittent fasting, may be an choice for many who have most cancers. However, people with most cancers must discuss to their physician and dietitian before starting a fasting food plan.
Sometimes referred to as the “satiety hormones”, one of many key ones is leptin which is launched from fat cells to suppress the manufacturing of ghrelin – mainly telling the physique “there may be fats here you could burn”. “We do not know exactly after we shift from glucose to ketones,” says Clarkson. “It depends on so many things – genetics, well being, way of life. How a lot glycogen you may have might be based on how a lot you’ve eaten and the way much vitality you have burned.” Additional research and larger scientific trials are wanted to determine whether or not intermittent fasting is beneficial in different methods and in the long term.
Intermittent fasting (IF) is a term used to explain a way of eating that cycles between periods of consuming and fasting. It has been gaining popularity lately due to its amazing well being benefits and easy to comply with practices. Intermittent fasting is a superb approach to complement an already healthy diet. But it’s important to know that you’ll solely achieve long-lasting well being advantages should you make fasting a half of your life-style. If you only goal for short-term weight reduction, fasting for a number of months could help you reach your targets.
On the brilliant side, this methodology has vital long-term fats loss benefits when you keep your meals parts the identical in your non-fasting days and maintain a well-balanced food plan. But in nature, mammals (and even hunter-gatherer anthropoids) have very completely different dietary habits. Their consuming patterns are less frequent than ours, they eat nutrient-dense foods, they usually naturally follow a form of intermittent fasting — simply as our early ancestors did. While train enhances outcomes, intermittent fasting can nonetheless be effective for weight loss and metabolic well being without it. Recent medical data signifies that combining intermittent fasting with traditional diabetes administration methods can result in vital enhancements in metabolic well being markers.
But as with every health strategy, personalization and skilled steering are key. Food is deeply social and cultural, and skipping meals could feel isolating. In some, fasting could set off nervousness, irritability, or unhealthy obsession with meals.
Many individuals use intermittent fasting to shed pounds as it’s a easy, handy, and efficient method to eat much less and reduce physique fat. Again, if you’re following time-restricted eating, know that you simply don’t have to maintain the identical consuming window daily. For instance, in case you have special brunch plans, then slide your window up to have the ability to take part — and feel happy and satisfied (not deprived) whereas intermittent fasting. When on IF, you’re simply eating throughout fewer time intervals, whether that be fewer hours within the day or fewer days of consuming. “In our analysis, we’ve found that time-restricted consuming naturally cuts out a number of hundred calories per day,” says Dr. Varady. That roughly leads to dropping about one to two pounds per week, she has observed in her research.
Other kinds of intermittent fasting contain lowering the amount you eat on sure days. As with any change in routine, it takes a quantity of days to adjust to intermittent fasting. Allow your self some flexibility as you determine a schedule that works for you. Fasting for eight hours may be simpler than 12, or you could choose to decrease your caloric intake a quantity of days of the week. While intermittent fasting appears to improve sleep quality, it could additionally result in sleep points depending on the timing of your meals. This is particularly true in the event that they eat late at night, which may increase the body’s temperature, which is the other of what usually happens throughout sleep.
Many diets promise fast weight loss however usually result in the “yo-yo” impact. One of the most important advantages of intermittent fasting is its simplicity. What we found was that the shift to fat burning and improved fat dealing with of the high-calorie meal had been near identical following each the traditional calorie-restricted “fast” day and the low-carb day. In different words, limiting carbs can elicit the same beneficial metabolic effects as fasting. If you take pleasure in eating as a social activity, it’s important to plan your fasting home windows or days round occasions like birthday parties, family meals, or dinner with friends.
Meta-analyses consolidate analysis findings, offering clearer evidence on the effectiveness of intermittent fasting. Pooling knowledge from various studies, meta-analyses determine patterns and tendencies within the well being impacts of fasting. Recent meta-analyses show that fasting might result in important improvements in weight loss, metabolic health, and persistent illness prevention. One research discovered a 91% elevated threat of cardiovascular disease dying for individuals following an 8-hour consuming window opens compared to those with the same quantity of extended period of eating.
Participants had been instructed to comply with a 25% calorie-reduced diet (1,500 to 1,800 energy per day for men and 1,200 to 1,500 calories per day for women) with a set ratio of energy from protein, carbs, and fats. Why would someone go for this way of consuming versus a regular food regimen, similar to going low carb or low fat? There are many types of intermittent fasting, all of which have profound well being advantages, including fats loss, improved coronary heart well being, and balanced insulin ranges. Intermittent fasting is a mealtime pattern of time-restricted consuming and fasting periods widely used for metabolic well being advantages. A trial from 2017 compared the impression of intermittent fasting and a typical calorie restriction food regimen on weight loss over 1 12 months. There have been no significant differences between the two groups for other markers of well being, similar to blood stress or heart rate.
In addition, some individuals experience excessive hunger and stress when following OMAD, which can result in overeating at mealtime. Intermittent fasting has been proven to induce autophagy, a survival mechanism by which the physique destroys damaged cells and recycles practical components for cellular restore. The study additionally suggests that elevated blood sugar levels, also called hyperglycemia, induced feelings of anger, unhappiness, and nervousness in diabetic girls. Watch the video under to be taught extra about the benefits of intermittent fasting and OMAD.
In mice, ketogenic food plan counteracted AD pathogenesis and cognitive decline, indicated by improved efficiency on studying and memory checks and decreased Aβ and tau pathologies 132. This information should offer you every little thing you should feel assured in meal planning while intermittent fasting. Although it may appear complicated proper now, fasting will turn into a behavior and part of your pure routine. Start sluggish and progressively work towards extra superior fasting protocols once you have discussed this selection along with your doctor. A green smoothie avoids the high-sugar content often present in fruit-based smoothies which is able to maintain you from getting on a blood-sugar rollercoaster. Smoothies are also nice for packing lots of wholesome fat into one meal.
Some consultants advocate the Mediterranean food plan, which includes plenty of healthy foods such as fish, fruit and greens, olive oil, entire grains, and nuts. Some studies have additionally found that members on intermittent fasting regimens lost muscle. Doctors additionally warning that some individuals who try intermittent fasting overeat on non-fasting days or hours. If you’re older, shedding too much weight might have an result on your bone well being, immune system, and your vitality stage.
Secure Your Home Network With Zero Trust Safety Greatest Practices
Employing a community segregation strategy is the greatest possible method to maintain this malware from infiltrating the the rest of your community. Each yr, more than 30 million people rely on us to keep their tech working. So whether it’s device setup and troubleshooting or enhancing your gadget’s performance, we’re here to assist.
Change your Wi-Fi password immediately and verify for signs of intrusion. Enable WPA2/WPA3 encryption and use a robust password to make this situation much less doubtless. For even more safety, configure a visitor community on your router to maintain your smart home devices firewalled off from more personal computing devices like laptops. Don’t neglect to activate your router’s firewall, found in its safety settings. A firewall screens all network traffic and may block unauthorized entry makes an attempt.
Broadband routers include built-in community firewalls and keep them enabled by default. Computers often also have their very own firewalls (such as Windows Firewall) in place. When you unpack a new router and plug it in for the primary time, Wi-Fi security might be disabled. Households can potentially install and run their Wi-Fi networks without activating appropriate safety safeguards. Most web suppliers supply a range of service plans at different worth points.
Smart residence devices can add some severe convenience to your life at house, but when the devices you’re using aren’t safe and correctly protecting your privacy, then the tradeoff is simply not worth it. Take the time to do your analysis on the devices you’re contemplating inviting into your home, your own personal house. Read CNET’s smart residence gadget critiques, seek for news about previous information breaches or privateness missteps. Finally, learn the producer’s privateness policy, particularly the section that deals with information assortment. Don’t depend on your devices’ default privacy settings to protect your privateness.
Through ADT’s partnership with Google, users can monitor their Google Nest cameras and video doorbells through the ADT Control app alongside their existing ADT security devices. This integration allows for centralized management and monitoring, giving owners a complete view of their home’s security standing. Users can obtain alerts, view live feeds, and even trigger actions similar to arming/disarming their safety system immediately from the ADT app, making certain a seamless and cohesive home safety expertise. Unused features on your smart units and cameras can introduce unnecessary security risks.
At just $49, the Echo Dot is half the worth of many of the different finest smart home hubs, making it a cheap funding for those just moving into good residence automation. While it lacks Zigbee or Z-Wave, if your smart residence devices have Bluetooth or Wi-Fi, this should not be an issue. And, it additionally works with Matter and as an extender if you have an eero mesh Wi-FI router.
A sensible residence refers to a convenient house setup where home equipment and devices could be automatically managed remotely from anyplace with an internet connection using a cellular or different networked system. Here you can choose your IOT community created earlier to assign this port to that network. Just make sure to verify that your other ports are not additionally modified. It can be a good idea to make sure the uplink port (the one related to your router or USG in my case) has this profile set to “All”. Otherwise the change will not be able to forward all the other networks to the router. You may additionally need to restart your device afterwards to select up the new community settings.
You can watch the digicam footage and control the working of all IoT devices, corresponding to lights, heating techniques, and door entry techniques. Once configured, take a look at the device’s functionality to ensure it operates appropriately. Check remote entry capabilities, automation features, and how the device interacts with other sensible devices on your network. To bolster security, change default passwords, allow two-factor authentication if obtainable, and guarantee your personal home network is safe with a powerful password and encryption protocols. To ensure a clean operation of smart devices and cameras on your home community, planning plays a crucial role.
Implementing two-factor authentication (2FA) wherever potential provides an extra layer of security, serving to to forestall unauthorized access even when a password is compromised. Regularly updating your passwords and avoiding the use of simply guessable data, corresponding to birthdays or widespread words, can additional improve the security of your good residence. Smart house gadgets are susceptible to cyber threats, just like another linked system.
Overall, this area is still evolving and the character of each system is consistently changing. The development of this subject is at present limited not only by know-how but also by a person’s capacity to trust a device and combine it successfully into his/her daily life. A house automation system will monitor and/or control house attributes corresponding to lighting, local weather, entertainment techniques, and appliances. It can also embrace residence safety such as entry management and alarm systems. Another commonplace safety mechanism, community firewalls, protects a home network from malicious traffic from the internet.
To shield your sensible house privateness, there are a number of important tips to observe. One key tip is to employ knowledge encryption methods to safe your sensible residence data. This means encrypting the information that is transmitted between your sensible residence gadgets and servers, making it rather more tough for hackers to intercept and decipher the data. However, privacy with IoT gadgets is not solely the duty of individuals. Manufacturers and repair suppliers also play a vital role in prioritizing data privateness and safety.
If managing your sensible house remotely isn’t important for you, disconnecting the hub from the internet is a powerful safety measure. This isn’t any cure-all, as complicated, multi-stage assaults will remain a menace, but no less than the most common-or-garden attacks will be prevented. Routers are like shipping providers on your network they usually determine where data is shipped and received.
Weak passwords and outdated software could make these networks susceptible to cyber hazards. Smart houses are susceptible to data breaches when delicate information saved in sensible devices is accessed, acquired, or disclosed with out permission. This sensitive data can embrace personal details, login credentials, and financial information.
This prevents attackers from accessing and manipulating your router’s settings from a distance. Most routers come with built-in firewalls that monitor incoming and outgoing visitors. Activate your router’s firewall to add an extra layer of safety against malicious activities. With a background in network engineering, Yacine breaks down digital threats, shares sensible advice to safe your units, and explores trends in cybersecurity. Minimizing the number of lively devices reduces your total assault surface.
It has dual pan-and-tilt cameras, coupled with a 2,000-lumen floodlight that can replace current out of doors lights. All of that tech takes energy, which implies this Eufy isn’t battery-powered. And since it is supposed to be placed up excessive, it doesn’t have a wall plug and must be hardwired into a lighting receptacle. I found it follows motion nicely, and it records clear audio and video. The Nest is our only choose that provides 24/7 recording to the cloud ($20 per 30 days or $200 per year). That means you can go back and verify the footage to see if the digicam missed someone or one thing stealing your packages.
The first and arguably probably the most critical step in bolstering your house network’s security is to secure your Wi-Fi router. This unassuming device serves as the entry level to your whole network, making it a main goal for cyberattacks. To ensure your digital fortress is strong, think about these essential steps in securing your router. Ensure that you just frequently replace all software program and firmware on your good gadgets. This practice helps patch safety vulnerabilities and retains your gadgets safe.
Its firewall filtering screens out the noise and rejects unsafe connections whereas letting normal connections function usually with no disruption. With four 1Gb Ethernet ports for native access and another 1Gb port for Internet connectivity, you might have loads of options to expand your community and hold your gadgets and information related safely. Its safety credentials are boosted by TP-Link Homecare which provides parental controls and built-in antivirus protection.
For about $100, you’ll receive a wise WeMo switch and a motion detector. Plug the swap into an electrical outlet, and then plug a tool, such as a lamp, heater or coffee pot into the swap. Pair the switch along with your smartphone utilizing Belkin’s app, and then you can control the switch remotely, letting you, for instance, flip a light on or off from 1,000 miles away (or just from your cozy bed). Intelligent lighting techniques, smart thermostats, and sophisticated house security solutions have all played a magistral role in serving to our homes become interconnected. In fact, these developments have created an ecosystem that permits us to turn into linked to our houses.
The majority of these suggestions are common-sense steps that anyone can take. Even the extra sophisticated ideas, similar to hiding the community or MAC handle filtering, solely require you to discover the options out there to you within the wifi router’s console. If you’re going on vacation or won’t be needing your home wifi community for a few weeks, you should flip it off.
Pay special attention to securing Internet of Things (IoT) units. Before exploring methods for securing your house community, absolutely grasp the profound implications of an unsecured network. A Smart Home refers to a residence that uses IoT gadgets for automating various tasks and providing enhanced functionalities to homeowners. These units have helped in the development of many organizations, companies, and agricultural developments.
Fortunately, there is no want to do that as lengthy as we’ve choices in the marketplace. I don’t own a single “smart” system or equipment aside from my phone, and I don’t really feel that I’m missing out at all or that smart gadgets would enhance my life in any means. I do fear a few time once we will have no choice however to purchase internet-enabled (and therefore inherently vulnerable) household home equipment. Securing your Wi-Fi Network with encryption protocols and strong passwords is important to prevent unauthorized access, defend knowledge transmission, and guarantee network safety.
By using these parts, you make your sensible residence protected, efficient, and simple to make use of. Remember, an excellent router is key since many gadgets use a lot of bandwidth. With the right setup, you’ll take pleasure in the benefits of residence automation.
Regular updates are vital for community safety; they typically include patches for newly found vulnerabilities. Imagine your home as a symphony and each linked system as an instrument. Smart houses operate through a centralized system—often your smartphone or a digital assistant—where you possibly can management everything from lights to locks with a easy command or a tap. It’s like having digital assistants scattered throughout you—thermostats that regulate themselves, fridges that order your groceries, or security cameras that ship live feeds to your cellphone.
Plus, putting in a safety system your self might help you save massive compared to professionally installed systems, even with established manufacturers like ADT. We’ve tested dozens of choices that will assist you discover the most effective DIY safety system on your residence. Taking benefit of security measures like two-factor authentication can make a giant difference. If the choice comes down to Frontpoint vs. SimpliSafe, understanding that the customer prefers DIY monitoring and only SimpliSafe offers this selection will make their decision simpler.
Signing a contract may not be best, however it could additionally come with free equipment or set up and decrease upfront costs. Berte suggested sticking with respected manufacturers and avoid being suckered in by low-cost unknown brands. “Often, these unknown brands minimize corners in development and manufacturing, including safety measures,” shared Berte. If your password won’t work or you see an unknown user in your account, somebody might have gained entry or tried to realize access to your community.
You must do the analysis to discover out whether the potential convenience, added safety, and cost financial savings over time outweigh the price of installing a full residence system. Consider utilizing particular person sensible residence products first to learn how properly they suit your way of life and finances. Smart homes can feature both wi-fi or hardwired techniques or both. Putting in a wi-fi home automation system with options similar to good lighting, local weather control, and safety can be limited to several thousand dollars, making it relatively affordable.
It ensures that all your devices work seamlessly and effectively inside your network setting. These cameras provide real-time video feeds that you could entry remotely. Some models even have movement detection capabilities and two-way audio for added performance. Once you’ve decided to set up smart units and cameras on your house network, understanding how they work is crucial. Smart gadgets, similar to good plugs, thermostats, and cameras, can greatly improve your home’s security and convenience. A visitor network isolates visitors’ or IOT devices from your major community, reducing safety risks and protecting delicate knowledge.
For instance, sensible doorbells can establish strangers and talk with them earlier than unlocking your front gate. The units have high-definition cameras that get mechanically activated by movement. Knowing tips on how to protect your router from hackers and different malicious intruders is essential. NETGEAR has been a safety leader within the WiFi trade since the Nineteen Nineties, when wi-fi routers have been first introduced for consumers. The custom continues and NETGEAR remains the trusted name for industry-leading router safety protocols and features. Just as a outcome of a device can hook up with the web doesn’t imply it ought to.
As a outcome, ADT has changed the name of Blue by ADT to ADT Self Setup. This new system is a brand new suite of security devices and methods which are fast and simple to arrange your self. Mirai is a cleverly designed program that takes benefit of our every day internet use vulnerabilities.
The security breach in smart home know-how happens in different ways and the diploma of damages varies according to what’s at stake. Here are a number of sensible residence technology dangers and what you can do to prevent them. By following these suggestions and staying alert, you can enjoy the advantages of a smart residence while decreasing the risks of cybersecurity threats.
Inside your router’s settings, navigate to the part related to wireless or Wi-Fi settings. Here, you’ll discover the option to allow a guest community, which is what you’ll use to create a separate network for your sensible gadgets. Once you’ve enabled the visitor network characteristic, you’ll find a way to configure it to your preferences. It’s an excellent practice to avoid using easily identifiable info like your name or address to boost safety.
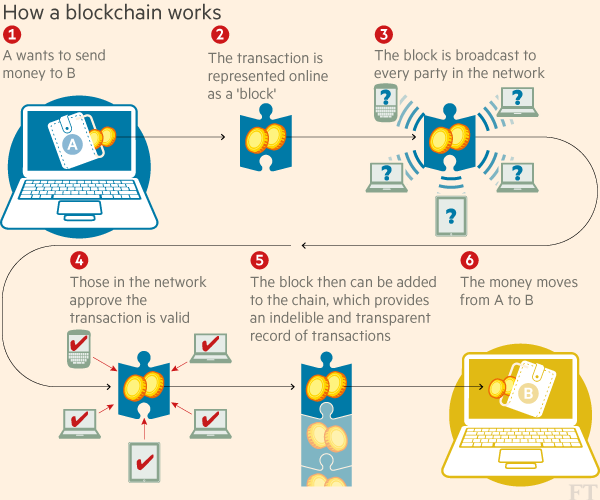
Solar panel add-ons are common for wireless cams, however Eufy has included its panel as a part of the design. Find a reasonably sunny place, and the digital camera will be capable of keep its battery charged throughout a lot of the year, saving you a step. Avoid common words or passwords that are easy to guess, corresponding to “password” or “123456.” Instead, use unique, complex passwords made up of letters, numbers, and symbols. You may also contemplate a password supervisor to up your safety sport. In Fortinet’s survey, 61 p.c of U.S.-based respondents mentioned the connected house would doubtless occur within the subsequent 5 years. Regardless of when the tipping point really hits, there isn’t any doubt that criminals shall be able to benefit from vulnerabilities.
This removes the risk of poorly secured IoT devices appearing as potential entry factors for hackers to compromise your computers or telephones. Trend Micro Home Network Security offers safety towards cyber-attacks for every Internet-connected device in your house – together with sport consoles, smart TVs, and home equipment. It additionally includes robust parental controls to keep your children safe on-line wherever they go.
If you’re coping with a DDoS assault, the place a quantity of methods overwhelm your community, contact your ISP immediately. Your router is the gateway to your smart home, so begin by shoring up its defenses. Activate essentially the most present type of encryption, ideally WPA3, to protect your knowledge as it travels by way of the airwaves. Your connected units work together to keep your home operating easily, ensuring each notice hits the proper pitch.
Its 4K Ultra HD resolution offers distinctive readability, while long-range Wi-Fi connectivity ensures reliable coverage over extensive outdoor areas. Powered by photo voltaic energy, it eliminates the necessity for frequent battery adjustments, making it eco-friendly and cost-effective. With a wire-free design, installation is easy, and superior motion detection sends immediate alerts to your smartphone.
Last 12 months at IFA 2024, we saw the Roborock Qrevo Curv, the ridiculous Yarbo Yard Robot, the daring new Nanoleaf Blocks, and the innovative Balcony Farm that aims to bring gardens to city environments. We’re expecting it to be another exceptional displaying for the smart house. We’ll be on the ground in Berlin exploring every little thing it has to supply starting on September 5, but here’s a quick take a look at what we’re hoping to see when the event kicks off. Moreover, it safeguards delicate data and accounts, together with email, banking, and social media, in opposition to unauthorized entry, guaranteeing the safeguarding of your digital existence.
Be creative, however avoid utilizing personal information like your name or address. After coming into the model new SSID, look for a “Save” or “Apply” button inside your router’s settings. Smart house gadgets supply comfort, security, and vitality efficiency by allowing you to control varied elements of your house remotely or through automation.
Some units enable for biometric login using a fingerprint or facial scan on your telephone, which is secure and handy. These options are not all the time on by default, so take the time to set them up. Hubs usually use a special expertise to attach units, one thing that is low energy, low bandwidth, and lengthy range. While some hubs are particular stand-alone units, it is growing extra frequent for producers to combine technologies like Thread into good audio system, shows, routers, and other gadgets. The trade-off is that hubs want energy and generally require an unused Ethernet port in your router to plug into. Because the Internet of Things is growing so quick, there’s lots of pressure on manufacturers to take advantage of that growth by getting as many merchandise on the market as they will.
Some house safety cameras have swappable batteries, while others have to be eliminated completely to be recharged. To ensure the house security cameras we’ve reviewed can be fairly in contrast, we’ve examined and analysed several essential options covering type, efficiency, and practicalities. Use it to narrow down your choices, then either hop right down to the more in-depth entry, or head straight to a retailer to buy.
Keep the following tips in mind to set up a protected community so as to take pleasure in your good devices safely. This separate network prevents devices that connect to it from seeing your major network. It’s price enabling this and connecting your smart devices to this community.
Home security is a significant concern for people all over the world. The international surveillance market has been growing swiftly in recent instances. Most properties install superior CCTV cameras to extend safety and security. Several companies present exceptional safety gadgets with cutting-edge features and versatile functionality.
Replace outdated units which may be not supported with patches, especially if they have known vulnerabilities. The world smart house market is set to succeed in a massive $154.4 billion by the top of 2024, and is anticipated to develop at an annual rate of 10.17% until 2029. This rapid adoption shows how deeply good know-how is being woven into our daily lives. Control4’s system works with gadgets from a broad range of manufacturers, including Samsung, LG, Dish, Sony, Yale, Kwikset, Sonos, Somfy, Apple and Roku.
Also, some corporations supply “visual verification,” which allows the monitoring middle to view cameras in case of an active alarm. Security techniques are efficient sufficient that insurance firms sometimes offer a reduction (between 5-20%) on home insurance premiums when you pay for professional monitoring. Abode offers more smart-home integration than some other security system we tested, which permits you to tie it into smart-home devices from different producers. As well as reducing safety risks, unplugging the router when you’re not there additionally prevents it from being damaged by power surges. Not only does this distribute community access extra evenly, it also helps to place your network out of reach/view from hackers.
Many manufacturers connect and embody monitoring services, so you’ll be alerted to any unusual or suspicious exercise, even when you’re not there. The drawback for lots of sensible units is that they’re controlled by way of apps or an internet interface, with access protected by a username and password. That signifies that hackers don’t have to the touch your hardware, but can try to acquire entry to your accounts and, due to this fact, your units.
Consumers count on smart-device vendors to take correct steps to secure the platform, Martincavage noted. But if the manufacturers don’t take security critically, or claim the underlying platform is “hacker-proof,” be cautious. Better-known manufacturers are less more likely to danger their reputations this way, he stated. Disable guest network access totally, and to be strict about who — or what — can get on the community. First, settle for that “you could be compromised,” Sherry warned, including that users should lock down as a lot as they can and spend money on fraud monitoring and id safety.
One minute you are basking within the security of your good home, and the next minute, you’re feeling insecure because of unauthorized access. A sensible house is important because it supplies advantages by way of comfort, effectivity, and security. With the power to remotely control and monitor different components of your house, you probably can take pleasure in enhanced comfort and peace of thoughts.
He oversees all evergreen content and oversees the Homes, Smart Home, and Fitness/Wearables categories for the positioning. In his spare time, he also checks out the most recent drones, electric scooters, and sensible residence gadgets, similar to video doorbells. Before his tenure at Tom’s Guide, he was the Reviews Editor for Laptop Magazine, a reporter at Fast Company, the Times of Trenton, and, many eons again, an intern at George journal.
Weatherproof development ensures sturdiness in numerous climates, and two-way audio permits for distant communication by way of the Swann Security app. Equipped with night imaginative and prescient and safe cloud storage choices, this camera offers round the clock surveillance and convenient entry to footage from anyplace. Compatible with the Swann Security app, it offers seamless integration for distant monitoring and customization of settings. These measures help shield your units from potential safety vulnerabilities. Securing your house Wi-Fi community is step one in protecting your good home. Start by changing the default password in your router to a powerful, unique password that contains a mixture of letters, numbers, and symbols.
A firewall acts as an extra layer of protection against malicious site visitors. It may be hardware or software-based and helps forestall unauthorized access to your network. Think of your home network as the muse of your good home’s safety. Every system you connect turns into one other room in the house, and each room has doors and home windows. One of the most important traps in good home adoption is believing that when a device is put in and working, your job is done. In actuality, security just isn’t a one-time setup; it’s a living, ongoing course of.
What your security techniques does within the event of an intrusion is determined by whether you’ve professional monitoring or not. When armed, motion sensors defend a given space by creating an invisible zone that cannot be breached without sounding an alarm. Common movement sensor know-how contains ultrasonic waves and passive infrared know-how. By enabling the Advance Content Controls superior browser safety settings, users can keep away from online threats before they even encounter them. Strong browser safety settings allow you to avoid threats from following harmful links online, such as phishing, drive-by links, and malware. Unless absolutely needed, disable remote management of your router.
This is a quick-and-easy method of connecting a new gadget to your router, and normally includes urgent a WPS button to effectively put the router into pairing mode, much like Bluetooth. Compatible devices will then recognize the pairing signal and routinely configure themselves. Place your router in a central location and away from windows to forestall unauthorized bodily access.
Go with the latter, and in case your community is already arrange on a different protocol, change it. WEP is weak and easy to crack, and whereas WPA2 positively isn’t good, it’s still vastly more secure than WEP. Many in style manufacturers supply native control by way of Matter, Thread, Zigbee, or their hubs. I switched them over after I realized what number of of my devices worked without the cloud. It reduce down on unnecessary web site visitors and made everything faster and more reliable.
In the absence of global security standards, there are concerns around privateness and data safety when utilizing IoT units. Home IoT techniques use AI to learn adjustments in the surroundings and alert users. Smart house devices usually work with voice instructions and observe the foundations of automation., and help in managing and monitoring things simpler for the users. The home automation techniques market is fast rising and is estimated to be value $63.2 billion by 2025.
In the latest variations of Windows, the firewall is automatically on and also you rarely must make any settings, but the identical is not true of all routers. Check your individual router by logging into the admin panel and looking for a firewall or firewall. Thankfully, logging in to the router’s admin panel from the web is normally turned off by default, but it’s nonetheless finest to check and turn it off if it’s nonetheless on.
The Asus ZenWiFi AX (XT8) is thought for its robust coverage and efficiency. Share your experiences or questions within the feedback, and for additional insights, especially on Alexa, visit our Alexa Archives. At CES 2022 in Las Vegas, privateness experts talk about privateness legal guidelines and the means to protect shopper information in the evolving digital age. Another security-focused bundle obtainable in SRM, Threat Prevention, inspects incoming and outgoing packets (internet traffic) and drops them if they’re malicious. ‡ Coverage consists of 99.9% of supply zip codes (excluding P.O. box, APO/FPO/DPO) by our largest retailer; in-warranty service only. All generations of eero products will work as wifi extenders for your Ring Alarm Pro, however we recommend eero 6 Mesh Wifi Extenders, that are appropriate with Ring Power Packs.
By doing so, you can benefit from the comfort and luxury of your good home whereas guaranteeing a high level of security. Sometimes, you may want to go away a big download running in a single day. However, more often than not, you aren’t going to be utilizing the network when you are asleep. It is a good suggestion to show off all electronics at night time and even unplug them.
Frontpoint’s name isn’t as recognizable as a few of the other names within the house security trade, like ADT or Ring, however the brand has set itself up to be a serious competitor on this area. Frontpoint doesn’t require a long-term contract, nevertheless it only offers skilled monitoring as a full-service residence security answer (no self-monitoring). Frontpoint monitoring service starts at $44.ninety nine per thirty days for a system without cameras, or $49.99 for a house safety system with cameras, which is relatively costly. Monitoring includes 24/7 help, quick response occasions, hourly automated system checks, an emphasis on privacy and security, and numerous other perks like alerts, sensor historical past, and video history. As for the safety itself, the Google gadgets do the similar old heavy lifting of movement detection, video capture, instant notifications, and so on., but ADT sets itself apart with its 24/7 professional monitoring. I by accident triggered the alarm a couple of times through the first month, and they called instantly to check in.
You may also want to keep entry to your bank account well away from the system. Some IoT gadgets are fairly restricted and only hook up with your control community. When you’re installing units, it’s a good idea to bookmark the producer’s web web page so you can simply verify for updates to the device’s firmware and software. If you are lucky, there shall be an e mail alert or even automatic updates; if not, you will have to look.
If you install a patch or a new version of software, or when you turn into conscious of something that may affect your device, reevaluate your settings to make sure they’re nonetheless acceptable. Any smart device in your house that uses electricity could be added to your home network and at your command. Whether you give that command by voice, remote management, pill or smartphone, the house reacts. Applications embrace smart lights, good audio system, smart locks, and good thermostats. Because smart residence systems require a live network connection, they are often hacked if the safety protocol is inadequate. Owners must be cautious about using sturdy passwords and updating software program as wanted.
Dive into this information and unlock the potential of your gadgets with ease. Smart properties can be safe properties — but provided that you’re taking the time to set issues up correctly. Avoid these widespread errors, and you’ll enjoy the comfort without putting your privacy in danger. Remember, a well-managed sensible house community is the cornerstone of a very environment friendly and connected house. We’ll delve into what good house networking is, its significance in your smart home ecosystem, and the different sorts of networks you’ll find a way to select from. The process of making separate VLANs or virtual native space networks may be very simple with Synology Routers.
Ai Techniques Can Be Hacked To Remove Safety Guardrails, Skilled Warns
Adding things like specific location information (GPS) won’t be perfect for everybody. EXIF knowledge comes immediately from your digicam and captures information like aperture, shutter pace, date and time, and the focal size. While this method presents proactive infringement detection, false positives/negatives are inevitable.
While some apps and web sites do their best to protect such data in their systems, hackers can discover methods to compromise such methods. With the tips under and lots of caution, your online data will be secure; removed from a hacker’s reach. Social media permits sharing of all aspects of life, nevertheless it’s essential to regulate who has access to the knowledge you share.
They could be lengthy at instances, however it’s price taking a second to protect your private info. Despite the dearth of an overarching information safety coverage, the US does have a number of privateness regulations that apply to sure data sorts. For example, The Privacy Act of 1974 dictates the gathering and use of non-public knowledge by federal companies.
As you’ll have the ability to see, there’s actually little you are able to do in terms of your info being spread online due to third-party entities. However, even with restricted control, there are still steps you presumably can take to protect your private information on-line. However, it can’t be denied that a few of the personal info you may have on the Internet is too sensitive or should be confidential, like your home handle, personal mobile number, etc. Your non-public data could possibly be used for doxxing, cyberbullying, stalking, blackmailing, harassment, hacking, and other dangerous acts. Being cautious with surprising messages and preserving safety software program up to date can protect against these threats.
If a suggestion appears too good to be true – corresponding to an internet stranger offering you free weapons or in-game currency – it’s most likely a scam. A Virtual Private Network (VPN) is a powerful device in your online privacy toolkit. A VPN encrypts your web connection, making it much harder for others to intercept and consider your online actions.
Review the software program you utilize regularly to ensure you are at all times operating the most recent model out there. Some companies, including the Chrome browser, can update routinely so you’ve the latest security measures and fixes. As part of these scams, victims sometimes obtain less money than requested however should repay the complete amount along with extraordinarily excessive rates of interest. Scammers additionally seek to govern enterprise listings by trying to add fraudulent contact numbers to impersonate public business profile listings.
Think twice before sharing data, and make sure that your knowledge does not end up on the dark net or in the hands of a stranger. As we interact on-line, we regularly share particulars about our lives, preferences, and actions. Social media platforms, for instance, encourage us to publish pictures, updates, and even our places. While this may be a good way to remain related with family and friends, it additionally will increase the chance of exposing personal data to people we might not know or belief. By training all these measures, your accounts, units, and knowledge are protected sufficient from cybercriminals.
Over 80 p.c of Americans worry about online security, however solely 50 percent of them search new ways to protect their on-line information. Protecting your on-line privacy ought to be a priority to ensure you’re maintaining yourself and your beloved ones protected from cyberattacks and scammers. In this guide, we’ll cover a few of the best methods to safeguard and defend your privateness on-line. Any data you enter on social networking web sites, accounts, or any other web site may doubtlessly be up for grabs within the event of an information breach. You’ll also want to examine sites frequented frequently plus social media networks so that when needed their profiles may be cleaned up. There isn’t any encryption on public Wi-Fi networks so anybody can snoop onto your connections and access your information.
Sure, it’s not a legal requirement in the US anymore, but it identifies you because the copyright holder and might help deter unauthorized use. The processes and costs of copyright registration vary around the globe, so it’s price checking what’s required the place you’re. But even when you never intend to set foot within the US, we highly suggest registering with the US Copyright Office (USCO). In some places, like the US, registering a picture can entitle you to damages for unauthorized use and should even get authorized bills covered. When you create something unique (like capturing real estate), you routinely turn into its copyright holder.
That’s why it’s essential to take the required steps to guard your photographs. You can even use Dark Web Monitoring providers like Identity Guard or Aura to see if any of your passwords have been leaked. Go to OptOutPrescreen.com, a service that removes your name from prescreened bank card and insurance offers. While there’s no method to remove all your private information from the internet, you can restrict what you share in the first place. Whenever you log in, you’ll want to provide your username, password, and one other authentication issue, corresponding to your Face ID or fingerprint. Even if hackers pay cash for your password, they won’t be able to access your account with out your face or fingerprint.
For these impacted by identification theft, the NSW Government has established ID Support NSW, a dedicated support service for people impacted by cybercrime and data compromise. ID Support NSW helps clients to acquire replacement Government issued identity paperwork as quickly and seamlessly as attainable. The NSW Government is taking proactive steps to make sure the individuals of NSW have the instruments they need to make certain the privateness and safety of their personal data. The NSW Digital ID will help to cease the overshare of data by placing people in charge of how and when their data is shared. Downloads are a main tactic hackers use to achieve entry to your network. And in a corporation, workers should want authorization earlier than downloading anything from the internet.
Permission Slip by Consumer Reports enables you to work through an “approved agent” to submit opt-out or deletion requests to knowledge brokers and other corporations routinely. In 2025, 74% of shoppers are aware of passkeys, and 69% have enabled passkeys on at least one account, exhibiting growing adoption of passwordless authentication. Regulatory and compliance risks are rising as related car options and knowledge flows elevate authorized issues beneath privacy legal guidelines, doubtlessly exposing firms to important regulatory fines. Data breaches and ransomware attacks are becoming more frequent and costly, with U.S. incidents now averaging over $10 million each in 2025.
Regardless of whether you sell, donate, or recycle an old device, you must take the time to properly wipe or encrypt any personal information which could be saved on it. Follow these directions so you don’t give away your data alongside along with your old gadgets. Read more of our guidance about tips on how to maintain your most delicate financial and well being knowledge secure.
Even if someone steals your password, they nonetheless can’t get in without that second key. Start with your most critical accounts – banking, e mail, and social media. Your future self will thanks when the following major breach hits the headlines. Companies don’t just hold this information locked away – they typically share it with third events, use it for targeted advertising, or store it in ways that make it weak to attacks.
Unless you consider that you’re underneath specific menace of targeted surveillance or digital attack, it isn’t essentially the most sensible tool for every day life. Physical safety of apparatus and places of work is essential even for purely online companies. Many organizations are turning to bodily safety solutions like ones listed here to ensure the protection of their tools and information throughout multiple areas. Unsubscribing from mailing lists helps protect your digital footprint by reducing the quantity of databases your personal knowledge, like your name and email address, is saved on. Fewer subscriptions imply there’s much less probability of your information being bought or uncovered in knowledge breaches, much less annoying spam, and a lowered risk of falling for a phishing rip-off. It’s vital to implement robust safety measures, similar to setting sturdy passwords and utilizing biometric authentication methods, if obtainable, to forestall unauthorized entry to your devices.
Encrypting delicate knowledge, corresponding to bank card numbers and bank account details, provides an extra layer of safety. Regularly monitor transactions for any unusual exercise and educate your users in regards to the significance of safe cost practices to additional defend financial information. One of the best forms of data safety practices to implement is password protection and authentication. Many massive firms undergo main data breaches that leak the login credentials of their clients, which may be simply discovered on the dark net. However, users can secure sensitive knowledge by implementing 2FA (two-factor authentication) or MFA (multi-factor authentication).
Implement role-based access controls—and often review permissions—and use logging systems to track who accessed data and when, guaranteeing full accountability and transparency. That way, if a data leak happens, the corporate can instantly see who was using the database last. Virtual personal networks (VPNs) are an efficient method to protect your data online. Free choices are often extraordinarily unsecure, they usually earn cash by utilizing your information in various methods. The greatest VPN for privateness is a premium VPN service that ensures that you are as protected as attainable on-line.
And sometimes, safety is breached, and prospects’ private knowledge gets out or gets destroyed. You might also not need your email tackle and cellphone quantity to be available to the public through your social media profiles. Restrict your contact particulars to ‘pals only’ and even make them fully personal.
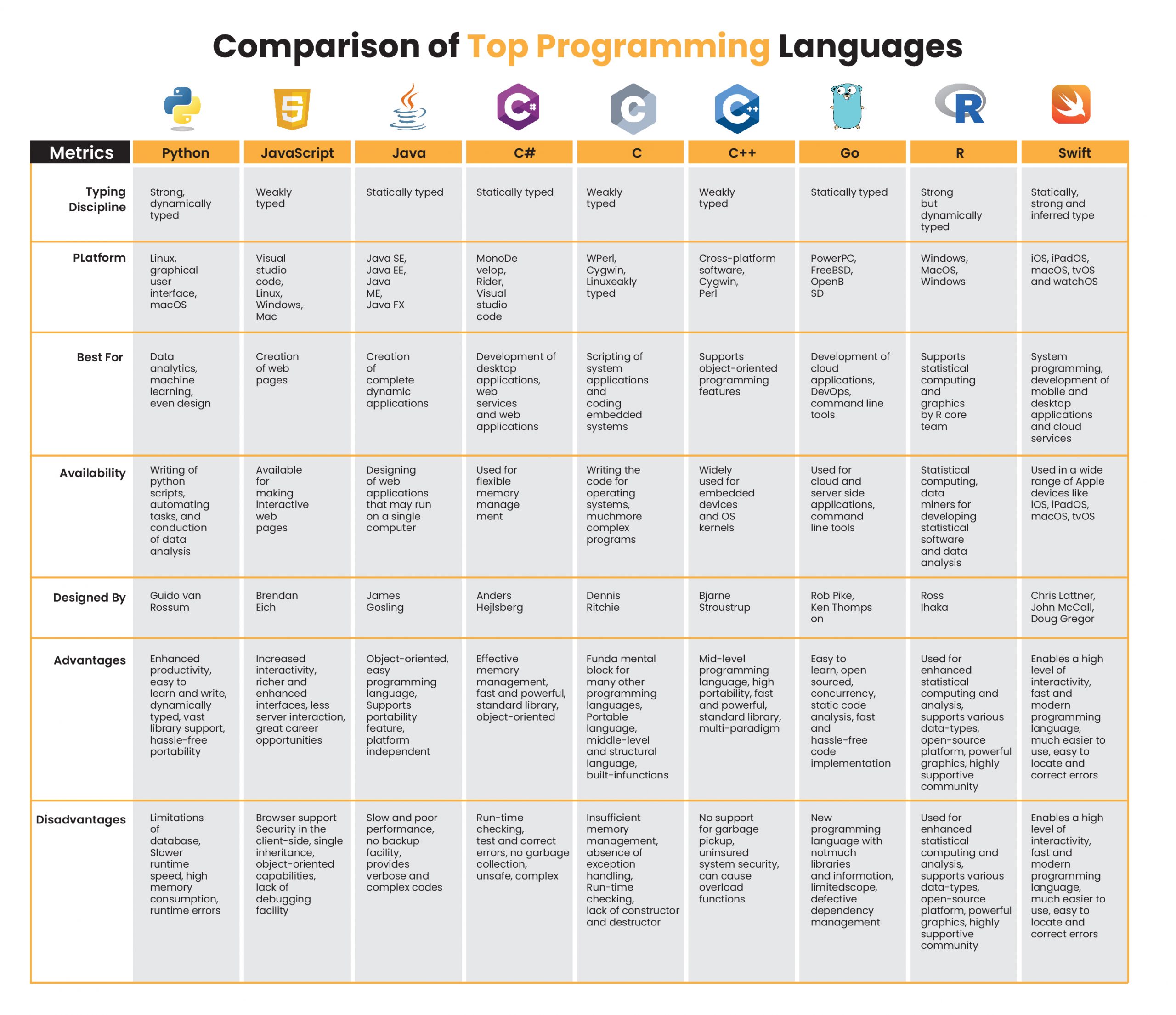
From smart TVs and voice assistants to fitness trackers and linked thermostats, the Internet of Things (IoT) has brought surveillance into our homes. These units often transmit user information back to producers or third-party services. Some even report conversations or acquire biometric knowledge like heart fee or sleep cycles. Facebook probably nonetheless has a shadow profile on you, built from your e-mail in someone else’s contact record or your face in a tagged photo. Google’s providers, likewise, observe your location history, search conduct, YouTube views, and app utilization.
Use a powerful and distinctive password with at least 20 characters, including numbers, letters, and symbols. Additionally, create a separate guest community and activate WiFi encryption, such as WPA3. Implement a router firewall, disable distant access, and keep your router’s software program up to date to stop hackers from having entry to your network.
Look for the vital thing indicators of a scan, similar to uncommon hyperlinks, spelling errors, or pressing requests for personal data. Go to each dealer’s website and discover opt-out or “delete your data/remove my info” hyperlinks, which are generally located in privacy insurance policies or buried in hard-to-find sections of their websites. Given that the us skilled over 3,200 information compromises in 2023, regular monitoring has turn out to be important for safeguarding your identity. They often promote or share this information with advertisers, insurers, financial establishments, and sometimes government our bodies with minimal oversight or client knowledge about these transactions. Common errors embrace mis-delivery of sensitive data, misconfiguration of cloud servers, or misuse of system privileges by licensed customers. Recent analysis from Pew Research Center reveals 71% of U.S. adults are concerned about how firms and authorities entities use their knowledge.
As for apps that rating poorly in online privacy but are still in style, consider eradicating them temporarily when not using them to limit their ability to trace your information. If you don’t want to do all of this manually, there are a quantity of tools that may assist, including Consumer Reports’ Permission Slip app, which handles users’ privateness rights requests on their behalf. You also can use DeleteMe, which helps remove users’ private information from open-source intelligence sites and other websites. From sensible home tech like doorbells and audio system to wearables like fitness trackers and VR headsets, lots of internet-connected devices collect consumer data.
Always double-check recipients before hitting “reply all” – especially when discussing private, skilled, or authorized matters. The more management you’ve over your social presence, the less doubtless it is to be used in opposition to you. If it’s something adverse, outdated, or way too private — you can take action. For a full breakdown, read our step-by-step guide to deleting your online presence.
She also encouraged people to see if their financial establishment offers the option of using a virtual credit or debit card. If your password for one website is hacked, it could possibly be used to get into your accounts for multiple sites. Data masking is similar to information encryption, however the main distinction is that it replaces the unique data with fictional knowledge to protect its safety.
But Facebook (which owns WhatsApp) can see who you talk with and when. This article supplies options for both low and high threat scenarios. You don’t should implement all of the suggestions, relying on your menace mannequin. Doaks knows firsthand how broadband powers crucial companies, like maintaining students related in school rooms and supporting care groups inside hospitals. “Cybersecurity is incredibly necessary as a result of it’s the one thing that may make connectivity inaccessible,” said Tracy Doaks, president and CEO of MCNC.
When you must hook up with public Wi-Fi try to always use VPN services. Use long passwords and whitelist (allow) solely your personal and household gadgets to join with it. This information may be tracked, stored, and potentially used to create a profile of your online identification. In the wrong hands, your digital footprint can open the door to privateness breaches, cyberattacks, and even id theft. And should you’re checking your bank card steadiness or transferring money between your checking and financial savings account while you’re on public Wi-Fi? These cybersnoops could nab your log-in credentials, giving them entry to your most important financial data.
Tailoring safety measures to particular information types ensures protection efforts are efficient and reliable. With Aura, your important data is monitored so you understand if anyone is using your online footprint for nefarious purposes. And if the worst happens, we provide 24/7 assist to assist you get your digital life again on observe.
From using anonymous searching modes to implementing robust passwords, these actionable ideas will empower you to navigate the digital world with confidence. Even if you’re cautious about what you submit, you might still be revealing yourself by way of metadata—such as timestamps, geolocation, contact networks, and system utilization. It’s not just what you share intentionally, but what your gadgets and apps are sharing in your behalf. Multi-factor authentication (MFA) retains your knowledge safe even when passwords are compromised.
Social media companies track your engagement patterns to construct detailed psychological profiles. They know your political opinions, your favorite manufacturers, your hobbies, even your sleeping patterns. A lot of oldsters think information privacy isn’t that essential as a result of they have “nothing to hide.” But the priority shouldn’t be whether data is exhibiting you doing anything wrong or secret. The concern is the extent to which companies combination that information and use that to make inferences about your habits or behaviors. We wish to present stories, bulletins, occasions, management messages and sources that are relevant to you.
Avoid Using Debit Cards for Online ShoppingDebit playing cards pull immediately from your checking account and provide less fraud protection than bank cards. Personal devices are the phones, tablets, laptops, and computers you use daily. They store private data and, for University neighborhood members, may contain access to delicate or work-related data. Keeping these devices safe helps defend both your privacy and the University’s digital environment. The online world provides super comfort but in addition carries dangers for privateness. Your clicks, interactions, and web site visits leave knowledge trails that always embrace your personal info.
It prevents you from shedding essentially the most important information in case your accounts are hacked; the information are deleted if the hardware breaks down or accidentally. They could be copied onto an external drive, but you could use cloud storage services like Google Drive, Dropbox, and OneDrive. That would make it important to again up your knowledge regularly so you will all the time have probably the most up to date model of your information. Older variations of the software you could have are a few of your most vital weaknesses on-line. The weak point in older versions is what most hackers use to realize entry into your computer systems and get hold of your information. It reduces the possibilities of getting cyber-attacks when you replace your software program to use the safety patches and fixes.
A wholesome interest within the darker side of digital will assist to ensure that when these menace actor techniques strategies procedures (TTPs) change, it won’t come as a surprise. It will certainly make it simpler for criminals to launch convincing phishing and other attacks. From sensible TVs to linked fridges, the trendy house is jam-packed with clever units. But if they’re web related, they may also be reached by hackers – who might hijack gadgets to conscript them into botnets that can be utilized to launch attacks on others. Hackers can target our units to steal knowledge and log-ins, maintain our system and information to ransom, enroll us in premium price companies, or earn cash from flooding the system with adware. “Start by speaking brazenly about on-line dangers like cyber-bullying and predators.
Examining the validity of net sites and confirming their knowledge safety practices ensures that materials is not disseminated to unreliable entities. It is crucial to determine and keep away from suspicious requests since email scams and fraudulent messages often attempt to trick prospects into disclosing login credentials or financial information. Unusual account habits often indicates attainable security breaches; hence, constant monitoring is a vital follow for safeguarding private information. Often undetectable until main harm outcomes, cybercriminals use financial knowledge via unauthorized transactions, id theft, and fraudulent purchases. Examining credit records, financial institution statements, and transaction history helps one establish suspicious exercise early on. Alerts and notifications from banks, fee techniques, and internet providers present customers with real-time updates on account exercise, due to this fact enabling speedy responses to unauthorized access.
Reducing the amount of knowledge you share helps mitigate these dangers. Weak passwords are simply guessed or cracked, which permit unauthorized entry to your accounts. Strong passwords are essential to protect any information that is saved inside these accounts. The most secure approach to protect knowledge is by encrypting it at all times.
However, if you’re willing to spend a while learning tips on how to navigate it, LogMeOnce is certainly one of the most feature-packed free password managers on the market. ZoogVPN has a stable free plan that you can get by registering and verifying your email. It gives you 10GB of data and 5 locations, in addition to apps for almost all in style units. A firewall is a software program program or piece of hardware that blocks hackers from entering and using your computer. Hackers search the web the method in which some telemarketers mechanically dial random telephone numbers.
Checking your e-mail while on public Wi-Fi risks exposing each your e mail contents and login details to cybercriminals. If they achieve access and take over your account, they’ll misuse it to launch attacks, spam, or different malicious activities. Surfshark’s different e mail allows you to generate alias email addresses that assist defend your id and keep your on-line actions separate.
By adopting PBAC, your group can enforce stricter controls and higher shield sensitive knowledge in an era where static roles not reflect dynamic workflows and security needs. A strong information classification policy is important for efficient data governance and risk administration, streamlining operations and making it simpler to safe sensitive information. By clearly defining how private or firm data ought to be dealt with and shared, it strengthens data privateness and protects against third- and fourth-party risks. Organizing information into clear categories additionally allows you to apply the right safeguards, scale back risk, and meet compliance goals more effectively. Data lineage tracks data’s journey across a quantity of techniques and purposes, serving to groups perceive its origins, the adjustments it undergoes, and its ultimate destination. Categorizing knowledge primarily based on sensitivity and figuring out how it’s used lets you implement focused safeguards.
Personal details operated by Whitepages, Spokeo, and PeopleFinder turn into part of their product choices for industrial distribution. One can submit requests to these sites to scale back their online accessibility. Unlike conventional monitoring strategies, AI is better at spotting new and hidden threats that may slip previous commonplace security measures. It significantly boosts your ability to safe delicate knowledge and has confirmed extremely effective in industries managing huge datasets.
These insurance policies should define the procedures for erasing knowledge and the forms of data that require secure erasure. Secure information erasure methods contain overwriting the prevailing information with new data, making it inconceivable to recuperate the unique info. These methods can include overwriting the information a number of instances, degaussing, or bodily destroying the storage media.
Schmidt in contrast right now’s AI race to the early nuclear era, a strong expertise with few global controls. “We want a non-proliferation regime,” he urged, so rogue actors cannot abuse these systems. This material is in all probability not printed, broadcast, rewritten, or redistributed. There are many cloud services you ought to use to backup your recordsdata, but it’s also a good suggestion to often use a physical onerous drive to store backups as well. In different words, hackers can either hack your gadget or they can hack your id. The Lepide Data Security Platform will discover and classify your important property and supports a variety of file types, together with Word, text, and Excel documents.
Keeping your software up-to-date protects you from the newest threats and enhances security. This practice safeguards your private data from unauthorized entry and potential breaches. A digital personal network (VPN) encrypts knowledge site visitors and acts as a protective tunnel between your device and the server. When using a quality VPN, you get an additional layer of security against hackers, web service suppliers, malicious web sites, and the government. By enabling automatic updates on your working system, browsers, and apps, you guarantee that your units are protected from the newest safety threats. This proactive strategy helps safeguard your delicate data from malware, ransomware, and different cyberattacks.
Those are nightmarish scenarios, to make certain, however privateness issues could broaden far past you as an individual, says Thomas Qitong Cao, assistant professor of expertise coverage at The Fletcher School. By securing your network and maintaining your gadgets up-to-date, you’ll have the ability to improve your cybersecurity and keep secure in today’s digital world. TitanFile is an award-winning safe file sharing and consumer collaboration platform. TitanFile is as straightforward to use as e mail, leading to increased efficiency, cost savings and better buyer satisfaction whereas bettering safety and compliance. TitanFile’s shoppers range from nationwide enterprises offering monetary, insurance, and legal providers, to authorities agencies and regulatory bodies, to small companies. If you’re going to use a public wifi community, at the naked minimum have a VPN on your gadget.
As phishing techniques evolve, staying knowledgeable and exercising warning can help you avoid turning into a target. This document is advisory in nature and is obtainable as a useful resource to be used together with your professional insurance coverage advisors in maintaining a loss prevention program. It is an summary only, and is not supposed as an various alternative to session along with your insurance dealer, or for legal, engineering or different professional recommendation. Before coming into private info into an net site, take a look at the top of your browser. If there is a lock symbol and the URL begins with “https,” that means the site is safe.
It delivers trusted privacy for all your devices, backed by a mission-driven firm that places people over earnings. However, you can use an anonymous e-mail service together with an online alias to forestall personal particulars from ending up in a knowledge leak. It’s important to use sturdy passwords on your gadgets and online accounts to keep away from hacking and getting your information stolen. So, use longer passwords with a combination of uppercase and lowercase characters. In addition to those online instruments, it’s important to note that organizations usually keep a knowledge warehouse the place they retailer large volumes of sensitive info. These warehouses could be prime targets for cybercriminals, so it’s vital that you just keep vigilant and take the required steps to protect your personal data.
Companies create incident response plans to handle security incidents and description proper subsequent steps to minimize the impression. Proactively managing the info lifecycle additionally helps organizations scale back the impression of knowledge breaches and enhance operational effectivity. You might have the strongest firewalls and most refined info technology (IT) tools potential, however none of that matters in case your staff unknowingly exposes delicate data. According to Verizon’s 2024 Data Breach Investigations Report, the “human element” — together with sincere worker mistakes — accounts for 68 percent of all data breaches. Did you know that Facebook can monitor virtually all of your net activity and tie it to your Facebook identity, even should you don’t have an account?
We provide hundreds of free resources, together with articles, movies, infographics, and toolkits on subjects like cybercrime, data privacy, and small enterprise security. These materials can be utilized to raise awareness and improve cybersecurity practices at residence, work, or within the community. It’s a reminder that online security and cybersecurity is a gaggle effort. No matter your business, job, or location, you’ve an element to play. Get involved and assist us empower a more secure interconnected world.
Symmetric encryption uses a single secret password or key to encrypt and decrypt information. The key could be a code or a random string of letters or numbers generated by a random quantity generator (RNG), which is typically required for banking-grade encryption. Symmetric algorithms are the best and most used form of encryption.
Our editors thoroughly review and fact-check each article to guarantee that our content material meets the best requirements. If we now have made an error or published misleading data, we’ll right or clarify the article. If you see inaccuracies in our content, please report the mistake by way of this form. Keeping your private information secure online is changing into more and more difficult in today’s ever-changing world. Every day, cybercriminals get more refined, and should you haven’t taken enough precautions, you’ll be a victim. The web is a dangerous place to be proper now due to how rapidly the world is evolving.
If you have passwords corresponding to, “123456,” “password,” “iloveyou,” “qwerty,” “starwars,” or “hello,” you’re removed from alone. That’s a problem since hackers might have the ability to simply guess your password. The actuality is that if you submit about your pets, even your first cat or hamster from 20 years ago, thieves can use that information to answer password or bank account problem questions.
The first and most important step to protect your photographs online is to register the copyright to your work. This will provide you with authorized proof of ownership and allow you to enforce your rights towards infringers. Before we dive into the tips, let’s review some basic terms that you have to find out about image protection. These act like digital signatures, embedding your information directly into the recordsdata. Some platforms even enable the disablement of right-click downloads for an additional layer of protection. Disabling right-click performance only helps with casual guests.
Digital privacy refers to the quantity of knowledge we make out there to online platforms, websites, and applications, and the way they use it. So, when you aren’t familiar with the time period web privacy, how are you going to take essential precautions? This article guides you about web privateness, how you can attain maximum privacy online, and essential steps to stay safe on-line. If you choose the “public visibility” option, anybody, from information scrapers to scammers, can view your page. However, with the “private” mode, you possibly can restrict access to those in your community. A VPN can encrypt your community information and conceal your IP handle, offering you with larger privateness when you’re accessing the internet.
It functions like an everyday e-mail except that you don’t must register and fill in your private information. A temporary mail is already obtainable once you open it, making it even faster to sign up for a website. Doing so lets you narrow down an assault towards only one of your accounts. But clicking on any malicious pop-up will redirect you to a harmful website, which mainly opens many different tabs or installs malicious software program in your gadget. In the previous, in case your cellphone was misplaced, you couldn’t do anything about it. All you want to do for that is activate the operate in ‘Settings’ as all smartphones have such a characteristic.
In fact, the less data you have on-line, the tougher it’s for id thieves to patch together strong information in your identification. Publicly obtainable info contained in your social media accounts can show criminals, stalkers, and anyone else the place (and with whom) you spend your time, in addition to what actions you take pleasure in. If you don’t see a way to close an account, attain out to the company’s support group and request that they delete your account and knowledge.
Make an effort of studying just a bit extra about privacy, safety and other relevant matters to ensure you know how to stay secure and tips on how to avoid pointless dangers. No device can clear up each drawback, but with data you can select those which might be right for you. Get conversant in the ways that malicious entities use social engineering and other methods to rip-off people and all the time be vigilant. When you know the way the trick works, it’s a lot simpler to avoid falling victim to it. Many features of online privateness are out of our control, but there are steps you can take to protect your data. Apple and Google, which collectively control a vast majority of the apps we have on our telephones, have beefed up their privateness permissions through the years.
Fewer accounts mean a smaller digital footprint and less for you to manage and defend. These two groups are particularly susceptible to on-line exploitation as they may underestimate the risks of sharing personal info online and could be simply manipulated. By maintaining your techniques and software current, you cut back the danger of being focused and having your personal information uncovered. If you choose a password that’s easy to guess, a malicious individual can easily entry your accounts.
You in all probability conduct on-line transactions corresponding to making purchases or bank deposits/transfers. Check that there’s a lock on your browser’s status bar earlier than you execute a transaction. The solution is data encryption software, which comes in both free and paid variations.
Instead, manually enter your information each time to reduce the chance of it being mechanically crammed in on a fraudulent web site. An exception to this rule would be using a password supervisor, which requires a master password. Websites and browsers allow you to save sensitive data such as passwords and credit card information for future use, but don’t save it.
Protecting your data from on-line threats is an important a half of navigating our digital world safely. While the online panorama can appear daunting, by constantly making use of these easy, actionable steps, you’ll find a way to significantly scale back your risk and acquire larger peace of thoughts. Start today – every small step you are taking makes your digital life safer.
Finally, the software should compile compliance reports and audit logs to facilitate adherence to data compliance legal guidelines and regulations. An app that requires entry to your digital camera, microphone, location providers, calendar, contacts, and social media accounts is a potential risk to your online privacy. As nicely as being aware of app permissions, consider deleting data, applications and accounts that you do not use anymore. The more applications or apps you have operating, the greater the prospect that one of them might be compromised.
Get involved and call your congressperson, he says — inform the policymakers that you simply care about online privateness. Soltani says he rarely recommends steps similar to utilizing ad blockers or VPNs for most individuals. They require too much attention and persistence to ship on privateness, and even then they’re limited in their effectiveness. There are legal guidelines round well being data and credit score and financial info, he explains, and a few states have Internet privacy-related legal guidelines. And if encryption matters to you, watch out about backing up your chats to the cloud.
Nearly every modern enterprise handles giant amounts of knowledge every single day. Knowing the method to access and handle this information whereas being aware of cybersecurity threats is a high-value skill. Staying safer on-line can feel like a challenge, however it doesn’t have to be. If you’re nonetheless studying how to protect your self towards on-line predators or scams, just deal with interactions on-line the identical means you would deal with interactions with a stranger walking down the road. That is, you in all probability wouldn’t open something they provide you, hand them your credit card, or lead them to your own home address.
It’s important to protect your wireless network at home or in the workplace. If you’re utilizing Windows, install updates for the working system. He has helped many people follow a career in knowledge science and expertise. He has labored with many several varieties of technologies, from statistical fashions, to deep learning, to giant language fashions.
It’s also all the time in personal searching mode, and you may lock the app itself behind a passcode. Tor is a community of proxies that allows you to access web sites in the deep internet whereas keeping you secure wherever you go. The proxies are maintained by volunteers, although, so their actual safety could be hit and miss. Web browsers usually enable promoting corporations to collect person knowledge.
If you don’t protect your on-line privateness, your personal particulars may fall into the mistaken palms. You might even give away your private information without realizing it. Here’s a breakdown of the reasons why your on-line privateness is essential.